Qualys Security Blog Expert network security guidance and news
- How Security Tool Misuse Is Reshaping Cloud Compromiseby Sayali Warekar on February 19, 2026 at 5:00 pm
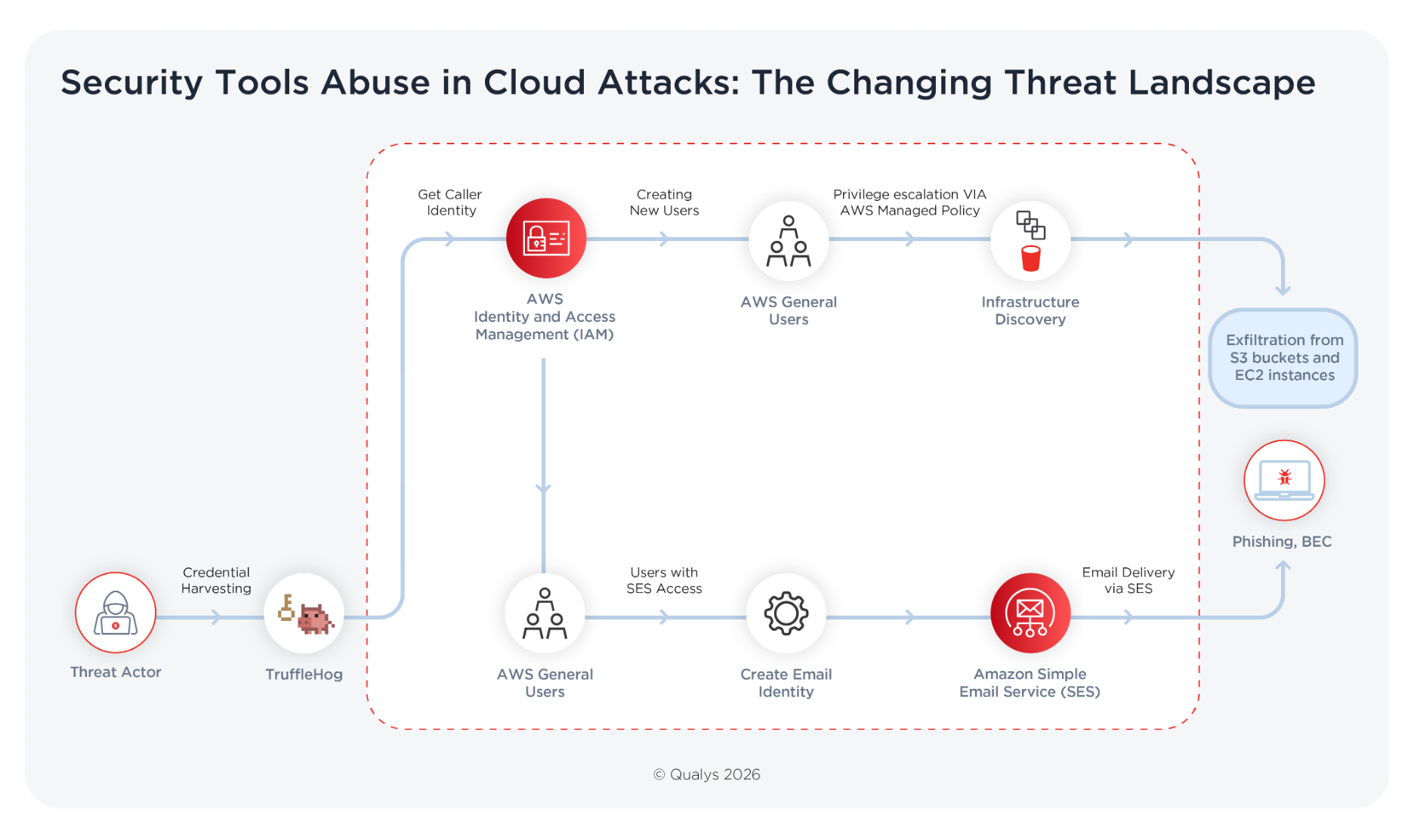
Key Takeaways Cloud Compromise Frequently Starts with Credential Misuse Cloud compromise is increasingly defined by authentication rather than exploitation. Exposed credentials and mismanaged identities now provide a faster path to access than vulnerability chaining. At the same time, legitimate security utilities designed to detect secret leaks are widely available. When used defensively, they reduce exposure.
- New: AI-Powered Patch Reliability Scoring—Predict Patch Impact Before You Deployby Eran Livne on February 18, 2026 at 9:35 pm
What do advisory USN-7545-1 and Windows updates KB5065426, KB5063878, KB5055523, and KB5066835 have in common? Based on anonymized Qualys telemetry from 2025, they were among the most frequently rolled-back patches, in other words, patches that had to be undone after deployment. Rollbacks aren’t just inconvenient—they’re disruptive. They burn time, trigger outages, and create security gaps
- Qualys Recognized as a Leader in the 2026 Forrester Wave™ for CNAPPby Kunal Modasiya on February 17, 2026 at 4:41 pm
Qualys’ Key Takeaways Selecting the right security platform is no longer just a technical decision; it’s a strategic imperative. For Chief Information Security Officers (CISOs) and cloud security leaders, the market is flooded with vendors promising total visibility and single-pane-of-glass simplicity. Cutting through the noise demands rigorous, objective analysis. For The Forrester Wave™: Cloud-Native Application Protection Solutions (CNAPP), Q1 2026,
- Active Directory Attacks Demystified: Pass-the-Hash (PtH), Pass-the-Ticket (PtT), and Beyondby Prashant Sheshnaryan Pawar on February 12, 2026 at 7:36 am
Key Takeaways Introduction Active Directory (AD) remains the backbone of identity and access management for most enterprises, controlling authentication, authorization, and access across users, endpoints, servers, and applications. Because of this central role, Active Directory is also one of the most targeted components in enterprise environments. Modern attackers rarely rely on noisy malware or brute-force
- Microsoft and Adobe Patch Tuesday, February 2026 Security Update Reviewby Diksha Ojha on February 10, 2026 at 8:51 pm
Microsoft’s February 2026 Patch Tuesday focuses on closing security gaps that attackers could exploit, reinforcing the importance of timely patching in enterprise environments. Here’s a quick breakdown of what you need to know. Microsoft Patch Tuesday for February 2026 This month’s release addresses 61 vulnerabilities, including five critical and 52 important-severity vulnerabilities. In this month’s updates, Microsoft has addressed six zero-day vulnerabilities that have been exploited in the wild. Microsoft addressed one vulnerability in Microsoft Edge (Chromium-based) that was patched earlier this month. Microsoft Patch Tuesday, February edition, includes updates for vulnerabilities in Microsoft Exchange Server, Microsoft Graphics Component, Windows
- TruConfirm: Autonomous, Agent-Led, Safe Exploit Validation for Real-World Risk Reductionby Himanshu Kathpal on February 4, 2026 at 5:00 pm
Key Takeaways The Question CISOs Cannot Answer Today The scan is done. Dashboards are full. Change windows are tight. And one critical question dominates every vulnerability review: “Is this exposure actually exploitable on our asset, in our production environment,with our controls, right now?” Volume is no longer an anomaly. In 2025, a staggering 48,177 CVEs were published. Most organizations now face thousands – often tens of thousands
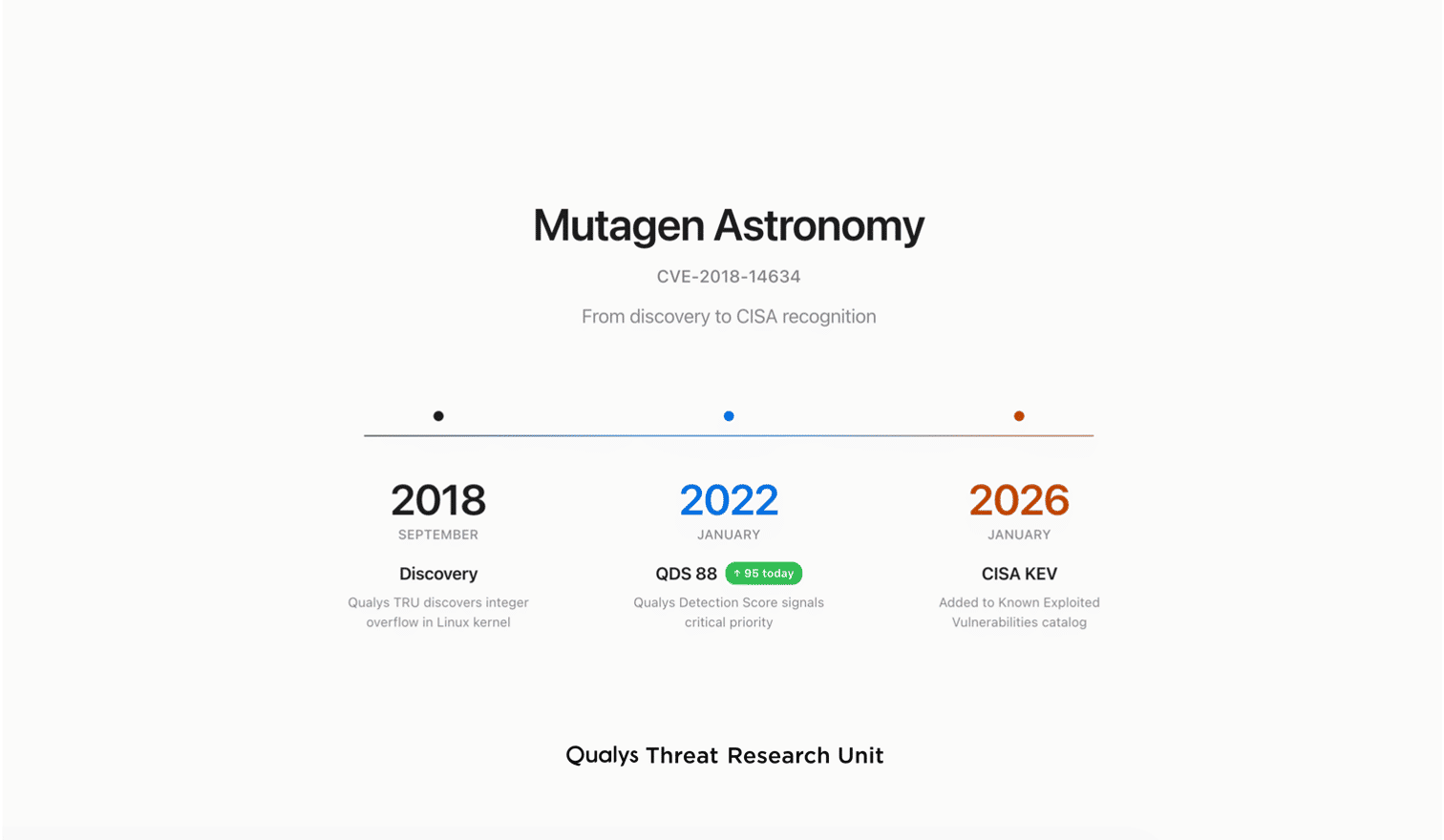
- Mutagen Astronomy: From Discovery to CISA Recognition—A Seven-Year Journeyby Saeed Abbasi on February 2, 2026 at 7:19 pm
Introduction On January 26, 2026, the Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2018-14634 to its Known Exploited Vulnerabilities (KEV) catalog. The same vulnerability was discovered by the Qualys Threat Research Unit (TRU) in September 2018. We nicknamed it “Mutagen Astronomy” as a tribute to the 1992 film Sneakers. In that movie, the phrase “Setec
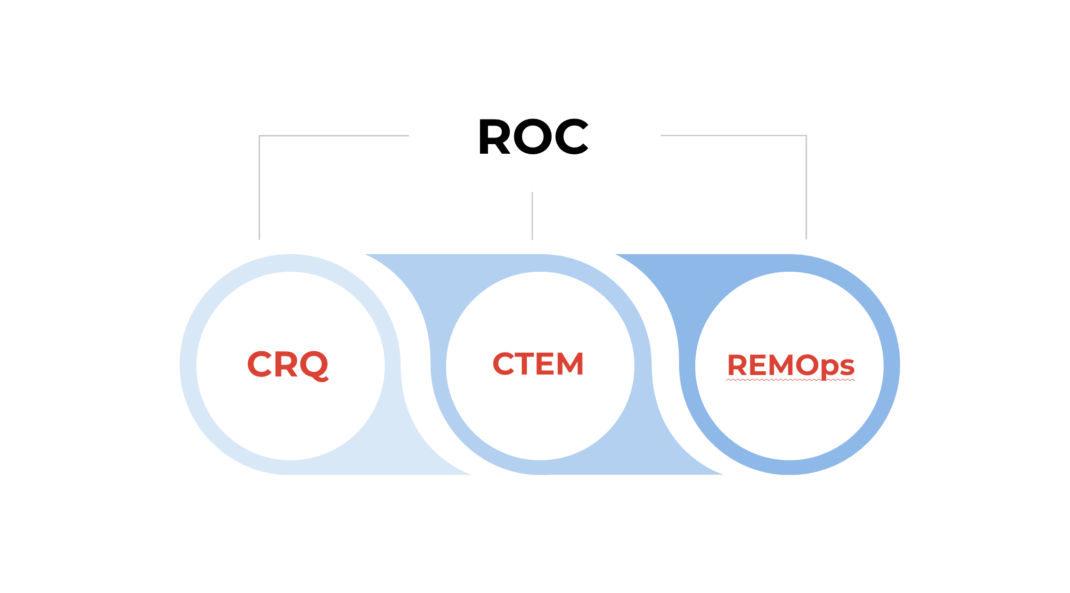
- ROC vs. CTEM: How a Risk Operations Center Evolves Beyond Continuous Threat Exposure Management in 2026by Shailesh Athalye on January 30, 2026 at 4:52 pm
Key Takeaways: The Essentials of ROC vs. CTEM Modern enterprises face a constant flood of data from dozens of siloed security tools, creating a fragmented view of risk. Continuous threat exposure management (CTEM) offers a framework to bring exposures together from these tools, and a risk operations center (ROC) provides the operational power to turn
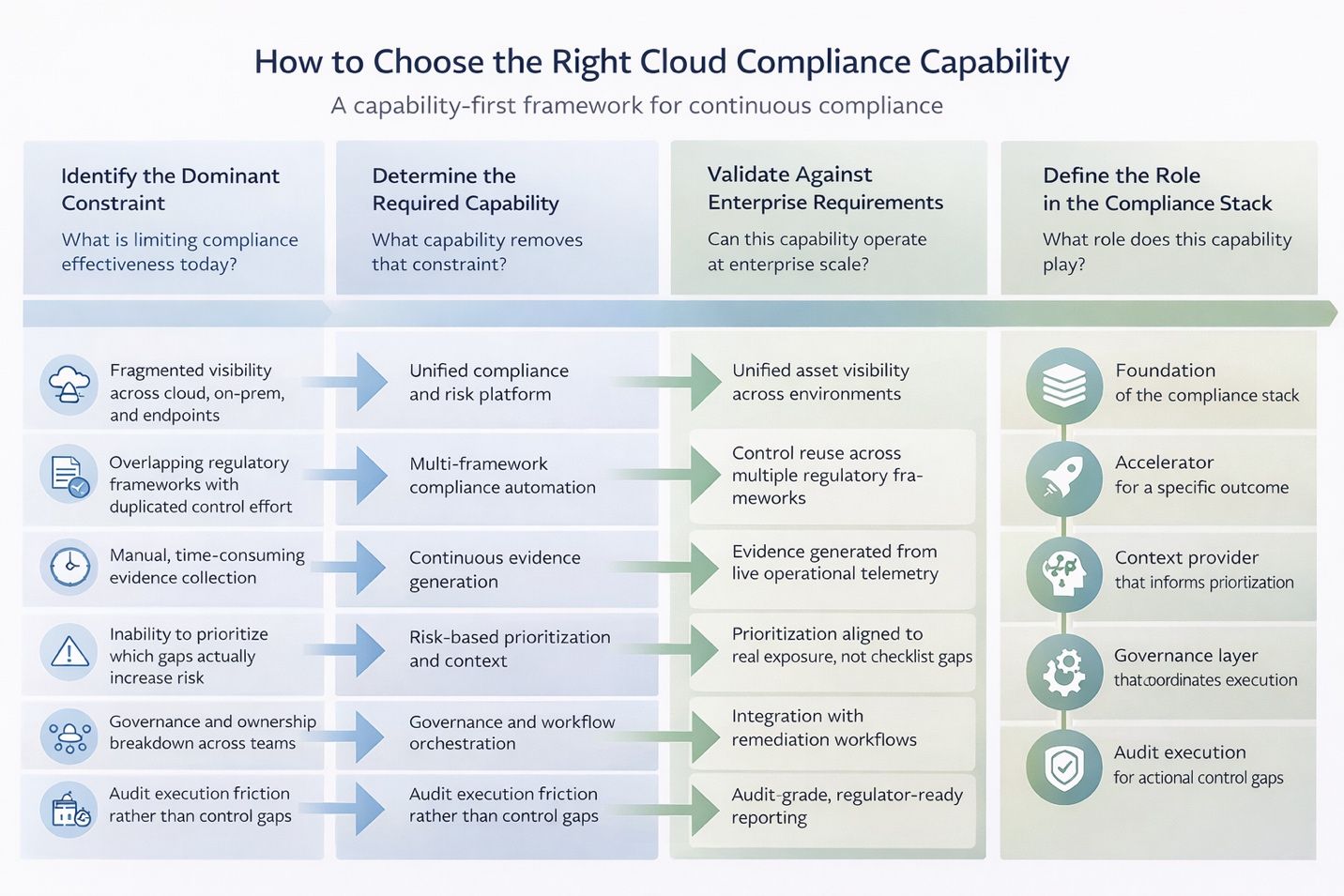
- Top 10 Cloud Compliance Tools for Enterprise Security and Audit Readiness in 2026by Pooja Prabhukhot on January 29, 2026 at 5:00 pm
Key Takeaways Compliance Breaks When Proof Lags Infrastructure Cloud compliance has changed. It is no longer an audit milestone. It is a continuous expectation. Boards demand visibility into regulatory exposure. Regulators expect evidence, not intent. Enterprise customers want assurance in real time. Meanwhile, frameworks such as NIST and CIS are becoming harder to implement as
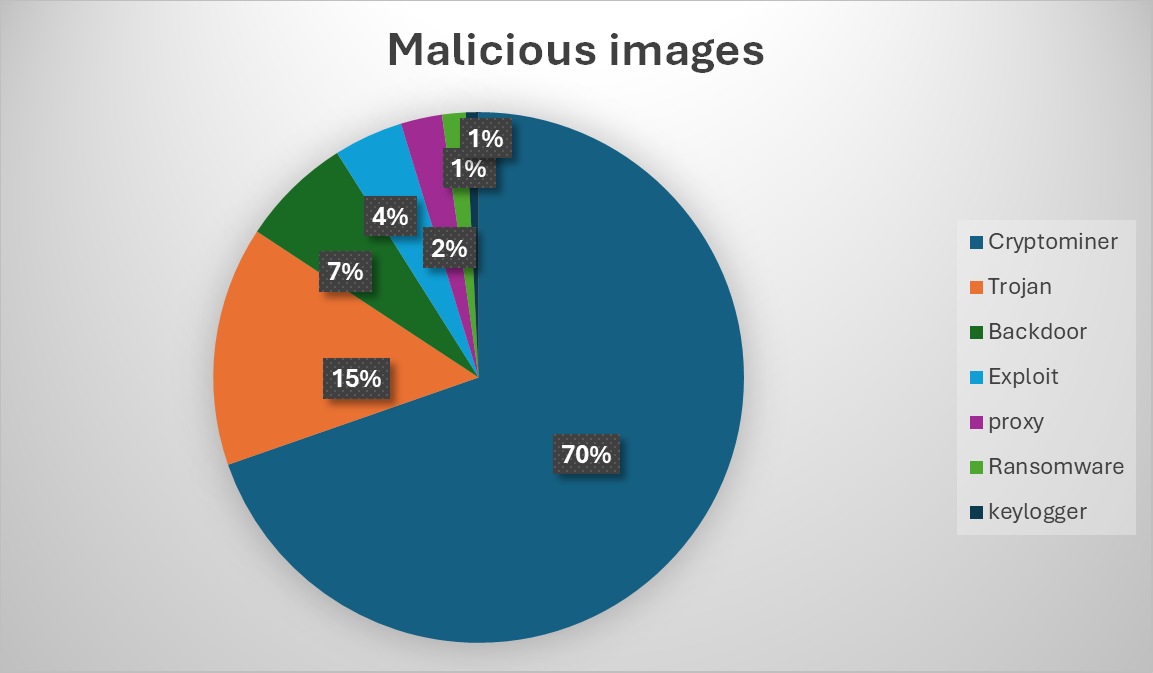
- How Public Container Registries Have Become a Silent Risk Multiplier in a Modern Supply Chainby Amit Gadhave on January 22, 2026 at 4:00 pm
Key Takeaways The Risk Introduced by Implicit Trust in Public Container Images Public container registries have become foundational to modern software development. A single docker pull can accelerate application delivery, standardize environments, and reduce operational friction across teams. However, that same convenience has quietly shifted trust decisions earlier in the development lifecycle, often without sufficient scrutiny of what is actually