XM Cyber Attack Path Management
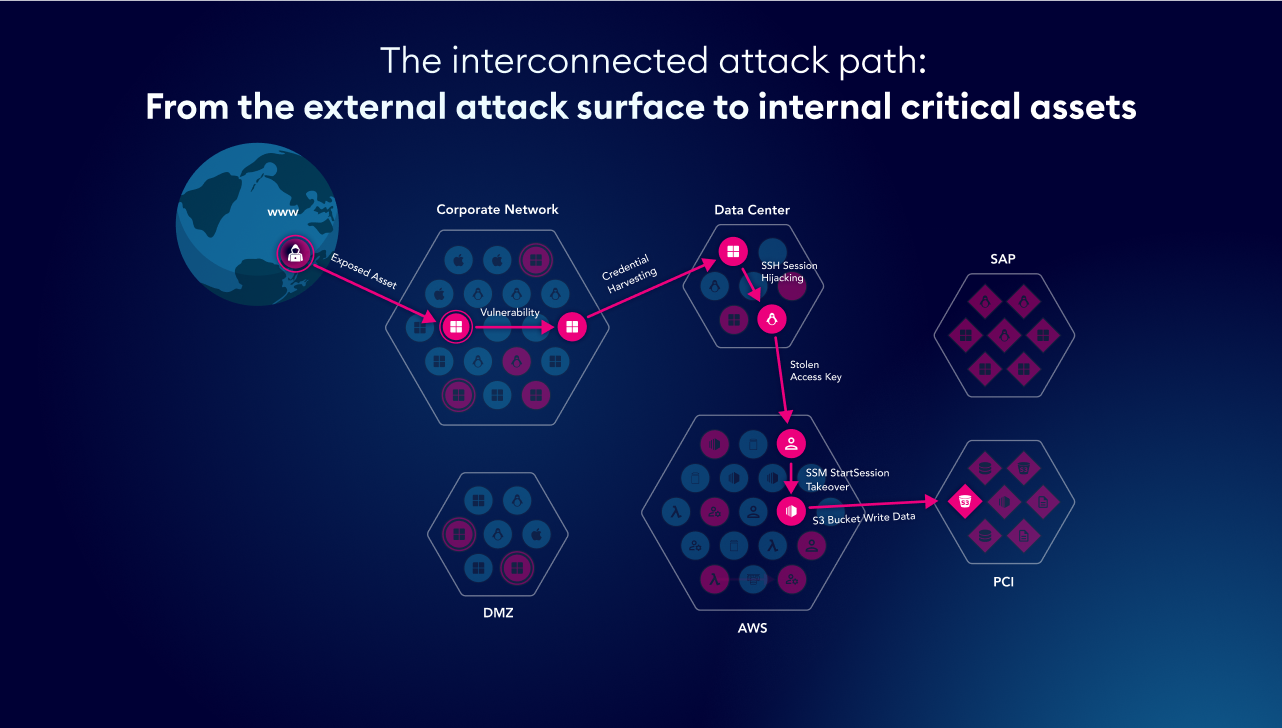
- Seeing Through the Eyes of An Attacker: Validating Exposures from External Breach Points to Internal Critical Assetsby hila.goldman@xmcyber.com on February 25, 2026 at 10:11 am
To catch a criminal, you need to think like a criminal. This is not a new concept, and it’s one that has been employed… The post Seeing Through the Eyes of An Attacker: Validating Exposures from External Breach Points to Internal Critical Assets appeared first on XM Cyber.
- Continuous Exposure Management Platformby XM Cyber on February 16, 2026 at 1:17 pm
Prevent Attacks that Put Your Business at Risk. As hybrid environments grow more complex, organizations are overwhelmed by a staggering volume of exposures. Traditional… The post Continuous Exposure Management Platform appeared first on XM Cyber.
- Beyond the Patch – Why Frost & Sullivan Named Us Leader for the 2nd Time in a Row in ASVby hila.goldman@xmcyber.com on February 12, 2026 at 9:53 am
It’s well known that security teams are often drowning in alerts. And considering that 74% of identified exposures are actually dead ends, i.e., they… The post Beyond the Patch – Why Frost & Sullivan Named Us Leader for the 2nd Time in a Row in ASV appeared first on XM Cyber.
- XM Cyber is the leader in Frost Radar™ 2026 Report for Automated Security Validation.by hila.goldman@xmcyber.com on February 12, 2026 at 9:26 am
Exposure validation is essential to filtering out noise and fixing what matters – and XM Cyber is helping organizations make that a reality. The post XM Cyber is the leader in Frost Radar™ 2026 Report for Automated Security Validation. appeared first on XM Cyber.
- Microsoft Office Zero-Day Vulnerability, CVE-2026-21509, Under Active Exploitationby hila.goldman@xmcyber.com on January 27, 2026 at 4:46 pm
Overview On January 26, 2026, Microsoft issued emergency out-of-band security patches for a high-severity security feature bypass vulnerability in Microsoft Office, tracked as CVE-2026-21509…. The post Microsoft Office <br> Zero-Day Vulnerability, CVE-2026-21509, Under Active Exploitation appeared first on XM Cyber.
- The Practical Path to Fixing What Matters: XM Cyber’s 2025 Milestones and What They Mean for Youby hila.goldman@xmcyber.com on January 26, 2026 at 12:11 pm
The cybersecurity industry has been driven by volume for years. More alerts, more scanners, and more “critical” vulnerabilities to patch. In 2025, this approach… The post The Practical Path to Fixing What Matters: XM Cyber’s 2025 Milestones and What They Mean for You appeared first on XM Cyber.
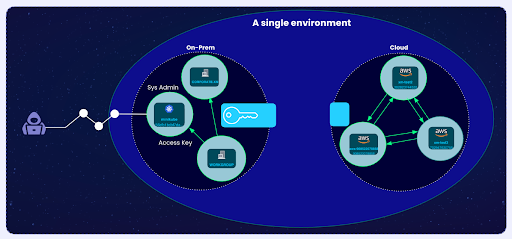
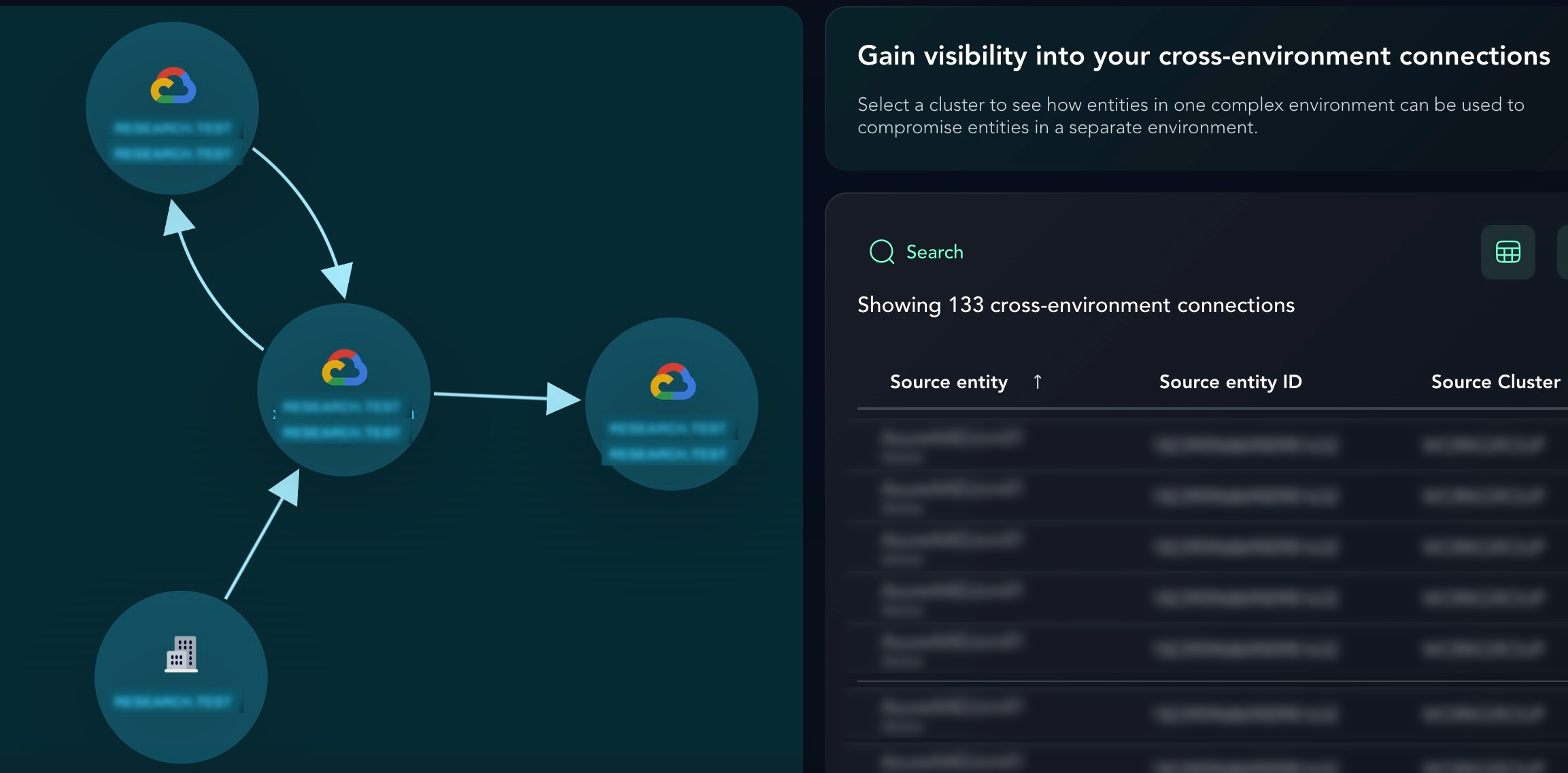
- XM Cyber External Attack Surface Managementby XM Cyber on January 21, 2026 at 10:05 am
Connect the Dots. Eliminate Risk From External Exposures. Bridge the gap between your external attack surface and your internal environment. Move beyond simple discovery… The post XM Cyber External Attack Surface Management appeared first on XM Cyber.
- Google Vertex AI security permissions could amplify insider threatsby hila.goldman@xmcyber.com on January 18, 2026 at 1:13 pm
A new way to escalate privileges inside Google’s Vertex AI highlights a broader problem: Enterprises have a level of trust in AI offerings that… The post Google Vertex AI security permissions could amplify insider threats appeared first on XM Cyber.
- Four Real-Life Financial Service Attacks Paths and How we Blocked Themby XM Cyber on January 18, 2026 at 6:40 am
Back in the wild west, there was this guy, Willie Sutton. Willie’s chosen profession wasn’t the town dentist-barber or saloon owner. Nope, he was… The post Four Real-Life Financial Service Attacks Paths and How we Blocked Them appeared first on XM Cyber.
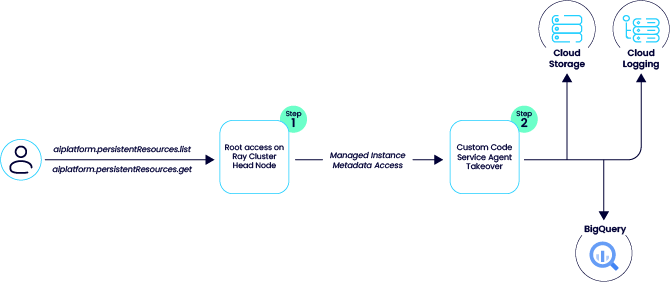
- Double Agent: Service Agent Privilege Escalation in Google Vertex AIby XM Cyber on January 15, 2026 at 8:18 am
While analyzing Google’s Vertex AI, we discovered two distinct attack vectors, specifically in Ray on Vertex AI and the Vertex AI Agent Engine, where default configurations allow low-privileged users to pivot into higher-privileged Service Agent roles. The post Double Agent: Service Agent Privilege Escalation in Google Vertex AI appeared first on XM Cyber.