Check Point Research Latest Research by our Team
- Caught in the Hook: RCE and API Token Exfiltration Through Claude Code Project Files | CVE-2025-59536 | CVE-2026-21852by samanthar@checkpoint.com on February 25, 2026 at 1:58 pm
By Aviv Donenfeld and Oded Vanunu Executive Summary Check Point Research has discovered critical vulnerabilities in Anthropic’s Claude Code that allow attackers to achieve remote code execution and steal API credentials through malicious project configurations. The vulnerabilities exploit various configuration mechanisms including Hooks, Model Context Protocol (MCP) servers, and environment variables -executing arbitrary shell commands The post Caught in the Hook: RCE and API Token Exfiltration Through Claude Code Project Files | CVE-2025-59536 | CVE-2026-21852<other cve=”” id=”” tbd=””></other> appeared first on Check Point Research.
- 2025: The Untold Stories of Check Point Researchby samanthar@checkpoint.com on February 23, 2026 at 3:27 pm
Introduction Check Point Research (CPR) continuously tracks threats, following the clues that lead to major players and incidents in the threat landscape. Whether it’s high-end financially-motivated campaigns or state-sponsored activity, our focus is to figure out what the threat is, report our findings to the relevant parties, and make sure Check Point customers stay protected. The post 2025: The Untold Stories of Check Point Research appeared first on Check Point Research.
- 23rd February – Threat Intelligence Reportby lorenf on February 23, 2026 at 9:01 am
For the latest discoveries in cyber research for the week of 23rd February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES France’s Ministry of Economy has disclosed a data breach resulted from an unauthorized access to the national bank account registry FICOBA, impacting information tied to 1.2 million accounts. Exposed data includes names, The post 23rd February – Threat Intelligence Report appeared first on Check Point Research.
- AI in the Middle: Turning Web-Based AI Services into C2 Proxies & The Future Of AI Driven Attacksby shlomoo@checkpoint.com on February 17, 2026 at 2:12 pm
Key Points Introduction AI is rapidly becoming embedded in day-to-day enterprise workflows, inside browsers, collaboration suites, and developer tooling. As a result, AI service domains increasingly blend into normal corporate traffic, often allowed by default and rarely treated as sensitive egress. Threat actors are already capitalizing on this shift. Across the malware ecosystem, AI is The post AI in the Middle: Turning Web-Based AI Services into C2 Proxies & The Future Of AI Driven Attacks appeared first on Check Point Research.
- 16th February – Threat Intelligence Reportby lorenf on February 16, 2026 at 5:57 pm
For the latest discoveries in cyber research for the week of 16th February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Dutch telecom provider Odido was hit by a data breach following unauthorized access to its customer management system. Attackers extracted personal data of 6.2 million customers, including names, addresses, phone numbers, email The post 16th February – Threat Intelligence Report appeared first on Check Point Research.
- 9th February – Threat Intelligence Reportby lorenf on February 9, 2026 at 12:50 pm
For the latest discoveries in cyber research for the week of 9th February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Romania’s national oil pipeline operator, Conpet, has suffered a cyberattack that disrupted its IT systems and took its website offline. The company said operational technology, including pipeline control and telecommunications systems, remained The post 9th February – Threat Intelligence Report appeared first on Check Point Research.
- Amaranth-Dragon: Weaponizing CVE-2025-8088 for Targeted Espionage in the Southeast Asiaby samanthar@checkpoint.com on February 4, 2026 at 1:57 pm
Key Points Introduction Check Point Research has identified several campaigns targeting multiple countries in the Southeast Asian region. These related activities have been collectively categorized under the codename “Amaranth-Dragon”. The campaigns demonstrate a clear focus on government entities across the region, suggesting a motivated threat actor with a strong interest in geopolitical intelligence. The campaigns The post Amaranth-Dragon: Weaponizing CVE-2025-8088 for Targeted Espionage in the Southeast Asia appeared first on Check Point Research.
- 2nd February – Threat Intelligence Reportby lorenf on February 2, 2026 at 1:35 pm
For the latest discoveries in cyber research for the week of 2nd February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES MicroWorld Technologies, maker of eScan antivirus, has suffered a supply-chain compromise. Malicious updates were pushed via the legitimate eScan updater, delivering multi-stage malware that establishes persistence, enables remote access, and blocks automatic The post 2nd February – Threat Intelligence Report appeared first on Check Point Research.
- Cyber Security Report 2026by samanthar@checkpoint.com on January 28, 2026 at 4:34 pm
The post Cyber Security Report 2026 appeared first on Check Point Research.
- 26th January – Threat Intelligence Reportby lorenf on January 26, 2026 at 1:35 pm
For the latest discoveries in cyber research for the week of 26th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES RansomHub ransomware group has claimed responsibility for a cyber-attack on Luxshare, an electronics manufacturer of Apple, Nvidia, LG, Tesla, and others. The threat actors claimed access to 3D CAD models, circuit board The post 26th January – Threat Intelligence Report appeared first on Check Point Research.
- KONNI Adopts AI to Generate PowerShell Backdoorsby samanthar@checkpoint.com on January 22, 2026 at 1:54 pm
Key Findings: Introduction Check Point Research (CPR) identified an ongoing phishing campaign that we associate with KONNI, a North Korean–linked threat actor active since at least 2014. KONNI is best known for targeting organizations and individuals in South Korea, with a focus on diplomatic channels, international relations, NGOs, academia, and government. The group typically relies The post KONNI Adopts AI to Generate PowerShell Backdoors appeared first on Check Point Research.
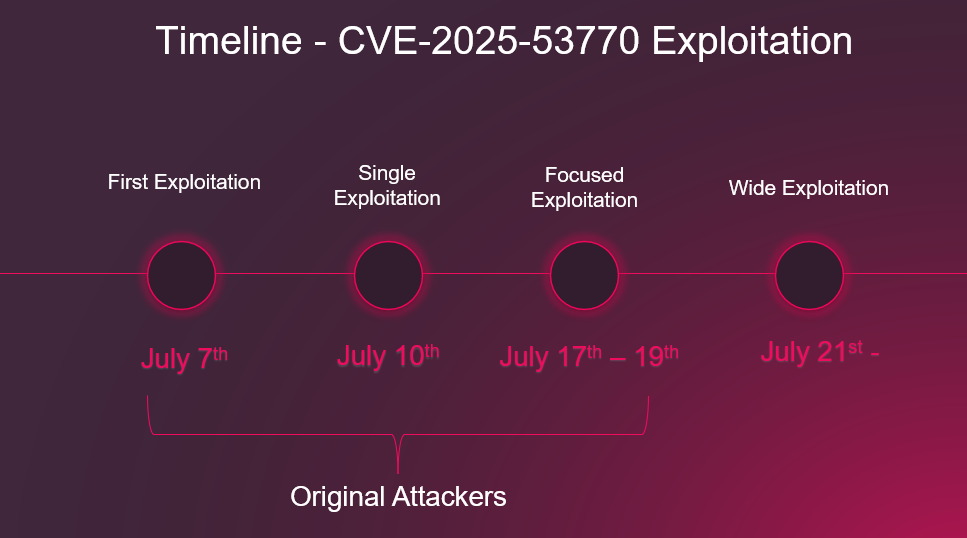
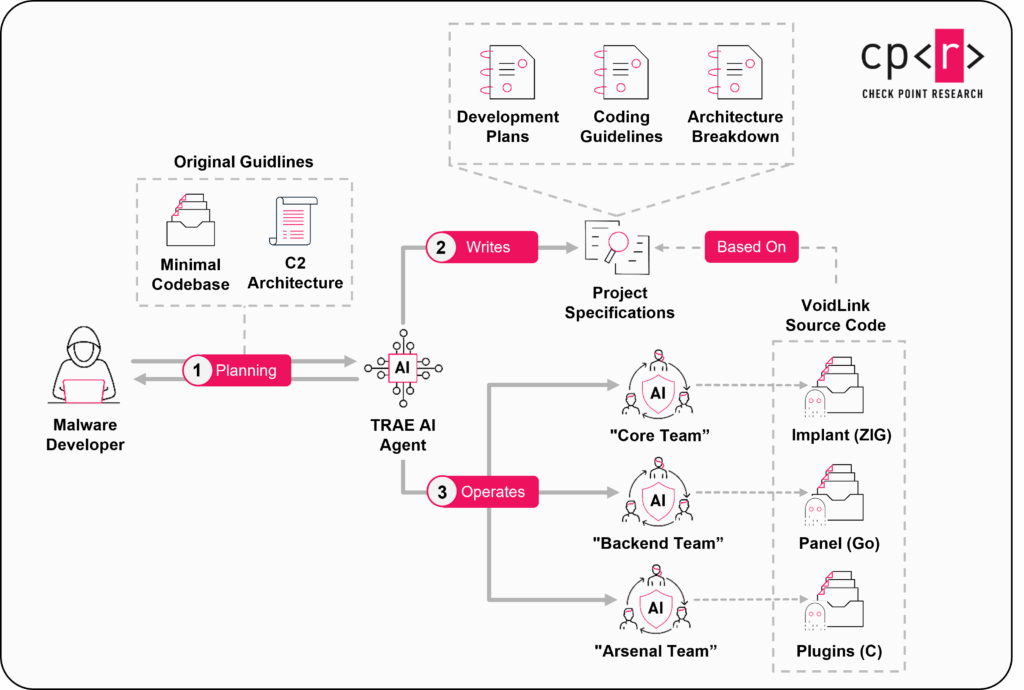
- VoidLink: Evidence That the Era of Advanced AI-Generated Malware Has Begunby samanthar@checkpoint.com on January 20, 2026 at 9:27 am
Key Points Introduction When we first encountered VoidLink, we were struck by its level of maturity, high functionality, efficient architecture, and flexible, dynamic operating model. Employing technologies like eBPF and LKM rootkits and dedicated modules for cloud enumeration and post-exploitation in container environments, this unusual piece of malware seemed to be a larger development effort The post VoidLink: Evidence That the Era of Advanced AI-Generated Malware Has Begun appeared first on Check Point Research.
- 19th January – Threat Intelligence Reportby tomersp@checkpoint.com on January 19, 2026 at 8:55 am
For the latest discoveries in cyber research for the week of 19th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Spanish energy company Endesa has disclosed a data breach after unauthorized access to a commercial platform used to manage customer information. Media report attackers listed over 1 terabyte of data, including IBANs, The post 19th January – Threat Intelligence Report appeared first on Check Point Research.