Espionage – The Cyber Express Trending Cybersecurity News, Updates, Magazine and More.
- Google Dismantles Massive Proxy Network That Hid Espionage, Cybercrime for Nation-State Actorsby Mihir Bagwe on January 29, 2026 at 8:45 am
Google dismantled what is believed to be one of the world’s largest residential proxy networks, taking legal action to seize domains controlling IPIDEA’s infrastructure and removing millions of consumer devices unknowingly enrolled as proxy exit nodes. The takedown involved platform providers, law enforcement and security firms working to eliminate a service that enabled espionage, cybercrime and information operations at scale. Residential proxy networks sell access to IP addresses owned by internet service providers and assigned to residential customers. By routing traffic through consumer devices worldwide, attackers mask malicious activity behind legitimate-looking IP addresses, creating significant detection challenges for network defenders. IPIDEA became notorious for facilitating multiple botnets, with its software development kits playing key roles in device enrollment while proxy software enabled attacker control. This includes the BadBox2.0 botnet Google targeted with legal action last year, plus the more recent Aisuru and Kimwolf botnets. Also read: Cloudflare Outage or Cyberattack? The Real Reason Behind the Massive Disruption The scale of abuse proves staggering. During just one week in January this year, Google observed over 550 individual threat groups it tracks using IP addresses associated with IPIDEA exit nodes to obfuscate their activities. These groups originated from China, North Korea, Iran and Russia, conducting activities including access to victim software-as-a-service environments, on-premises infrastructure compromise and password spray attacks. “While proxy providers may claim ignorance or close these security gaps when notified, enforcement and verification is challenging given intentionally murky ownership structures, reseller agreements, and diversity of applications,” Google’s analysis stated. Google’s investigation revealed that many ostensibly independent residential proxy brands actually connect to the same actors controlling IPIDEA. The company identified 13 proxy and VPN brands as part of the IPIDEA network, including 360 Proxy, ABC Proxy, Cherry Proxy, Door VPN, IP 2 World, Luna Proxy, PIA S5 Proxy and others. The same actors control multiple software development kit domains marketed to app developers as monetization tools. These SDKs support Android, Windows, iOS and WebOS platforms, with developers paid per download for embedding the code. Once incorporated into applications, the SDKs transform devices into proxy network exit nodes while providing whatever primary functionality the app advertised. Google analyzed over 600 Android applications across multiple download sources containing code connecting to IPIDEA command-and-control domains. These apps appeared largely benign—utilities, games and content—but utilized monetization SDKs enabling proxy behavior without clear disclosure to users. The technical infrastructure operates through a two-tier system. Upon startup, infected devices connect to Tier One domains and send diagnostic information. They receive back a list of Tier Two servers to contact for proxy tasks. The device then polls these Tier Two servers periodically, receiving instructions to proxy traffic to specific domains and establishing dedicated connections to route that traffic. Two-Tier C2 Infrastructure. (Source: Google Threat Intelligence) Google identified approximately 7,400 Tier Two servers as of the takedown. The number changes daily, consistent with demand-based scaling. These servers are hosted globally, including in the United States. Analysis of Windows binaries revealed 3,075 unique file hashes where dynamic analysis recorded DNS requests to at least one Tier One domain. Some posed as legitimate software like OneDriveSync and Windows Update, though IPIDEA actors didn’t directly distribute these trojanized applications. Residential proxies pose direct risks to consumers whose devices become exit nodes. Users knowingly or unknowingly provide their IP addresses and devices as launchpads for hacking and unauthorized activities, potentially causing providers to flag or block them. Proxy applications also introduce security vulnerabilities to home networks. When a device becomes an exit node, network traffic the user doesn’t control passes through it. This means attackers can access other devices on the same private network, effectively exposing security vulnerabilities to the internet. Google’s analysis confirmed IPIDEA proxy software not only routed traffic through exit nodes but also sent traffic to devices to compromise them. Google’s disruption involved three coordinated actions. First, the company took legal action to seize domains controlling devices and proxying traffic through them. Second, Google shared technical intelligence on discovered IPIDEA software development kits with platform providers, law enforcement and research firms to drive ecosystem-wide enforcement. Third, Google ensured Play Protect, Android’s built-in security system, automatically warns users and removes applications incorporating IPIDEA SDKs while blocking future installation attempts. This protects users on certified Android devices with Google Play services. Google believes the actions significantly degraded IPIDEA’s proxy network and business operations, reducing available devices by millions. Because proxy operators share device pools through reseller agreements, the disruption likely impacts affiliated entities downstream. Also read: What Is a Proxy Server? A Complete Guide to Types, Uses, and Benefits The residential proxy market has become what Google describes as a “gray market” thriving on deception—hijacking consumer bandwidth to provide cover for global espionage and cybercrime. Consumers should exercise extreme caution with applications offering payment for “unused bandwidth” or “internet sharing,” as these represent primary growth vectors for illicit proxy networks. Google urges users to purchase connected devices only from reputable manufacturers and verify certification. The company’s Android TV website provides up-to-date partner lists, while users can check Play Protect certification status through device settings. The company calls for proxy accountability and policy reform. While some providers may behave ethically and enroll devices only with clear consumer consent, any claims of “ethical sourcing” must be backed by transparent, auditable proof. App developers bear responsibility for vetting monetization SDKs they integrate.
- AWS Blames Russia’s GRU for Years-Long Espionage Campaign Targeting Western Energy Infrastructureby Mihir Bagwe on December 16, 2025 at 11:19 am
Amazon Web Services (AWS) has attributed a persistent multi-year cyber espionage campaign targeting Western critical infrastructure, particularly the energy sector, to a group strongly linked with Russia’s Main Intelligence Directorate (GRU), known widely as Sandworm (or APT44). In a report released Monday, the cloud giant’s threat intelligence teams revealed that the Russian-nexus actor has maintained a “sustained focus” on North American and European critical infrastructure, with operations spanning from 2021 through the present day. Misconfigured Devices are the Attackers’ Gateway Crucially, the AWS investigation found that the initial successful compromises were not due to any weakness in the AWS platform itself, but rather the exploitation of customer misconfigured devices. The threat actor is exploiting a fundamental failure in network defense, that of, customers failing to properly secure their network edge devices and virtual appliances. The operation focuses on stealing credentials and establishing long-term persistence, often by compromising third-party network appliance software running on platforms like Amazon Elastic Compute Cloud (EC2). AWS CISO CJ Moses commented in the report, warning, “Going into 2026, organizations must prioritize securing their network edge devices and monitoring for credential replay attacks to defend against this persistent threat.” Persistence and Credential Theft, Part of the Sandworm Playbook AWS observed the GRU-linked group employing several key tactics, techniques, and procedures (TTPs) aligned with their historical playbook: Exploiting Misconfigurations: Leveraging customer-side mistakes, particularly in exposed network appliances, to gain initial access. Establishing Persistence: Analyzing network connections to show the actor-controlled IP addresses establishing persistent, long-term connections to the compromised EC2 instances. Credential Harvesting: The ultimate objective is credential theft, enabling the attackers to move laterally across networks and escalate privileges, often targeting the accounts of critical infrastructure operators. AWS’s analysis of infrastructure overlaps with known Sandworm operations—a group infamous for disruptive attacks like the 2015 and 2016 power grid blackouts in Ukraine—provides high confidence in the attribution. Recently, threat intelligence company Cyble had detected advanced backdoors targeting the defense systems and the TTPs closely resembled Russia’s Sandworm playbook. Read: Cyble Detects Advanced Backdoor Targeting Defense Systems via Belarus Military Lure Singular Focus on the Energy Supply Chain The targeting profile analyzed by AWS’ threat intelligence teams demonstrates a calculated and sustained focus on the global energy sector supply chain, including both direct operators and the technology providers that support them: Energy Sector: Electric utility organizations, energy providers, and managed security service providers (MSSPs) specializing in energy clients. Technology/Cloud Services: Collaboration platforms and source code repositories essential for critical infrastructure development. Telecommunications: Telecom providers across multiple regions. The geographic scope of the targeting is global, encompassing North America, Western and Eastern Europe, and the Middle East, illustrating a strategic objective to gain footholds in the operational technology (OT) and enterprise networks that govern power distribution and energy flow across NATO countries and allies. From Cloud Edge to Credential Theft AWS’ telemetry exposed a methodical, five-step campaign flow that leverages customer misconfiguration on cloud-hosted devices to gain initial access: Compromise Customer Network Edge Device hosted on AWS: The attack begins by exploiting customer-side vulnerabilities or misconfigurations in network edge devices (like firewalls or virtual appliances) running on platforms like Amazon EC2. Leverage Native Packet Capture Capability: Once inside, the actor exploits the device’s own native functionality to eavesdrop on network traffic. Harvest Credentials from Intercepted Traffic: The crucial step involves stealing usernames and passwords from the intercepted traffic as they pass through the compromised device. Replay Credentials Against Victim Organizations’ Online Services and Infrastructure: The harvested credentials are then “replayed” (used) to access other services, allowing the attackers to pivot from the compromised appliance into the broader victim network. Establish Persistent Access for Lateral Movement: Finally, the actors establish a covert, long-term presence to facilitate lateral movement and further espionage. Secure the Edge and Stop Credential Replay AWS has stated that while its infrastructure remains secure, the onus is on customers to correct the foundational security flaws that enable this campaign. The report strongly advises organizations to take immediate action on two fronts: Secure Network Edge: Conduct thorough audits and patching of all network appliances and virtual devices exposed to the public internet, ensuring they are configured securely. Monitor for Credential Replay: Implement advanced monitoring for indicators of compromise (IOCs) associated with credential replay and theft attacks, which the threat actors are leveraging to move deeper into target environments.
- US Offers $10M for Iranian Cyber Operatives Behind Election Interference and Critical Infrastructure Attacksby Mihir Bagwe on December 3, 2025 at 7:25 am
Fatemeh Sedighian Kashi and Mohammad Bagher Shirinkar maintain a close working relationship coordinating cyber operations targeting elections, US critical infrastructure and businesses through the Iranian Revolutionary Guard Corps cyber unit known as Shahid Shushtari. The U.S. Department of State announced rewards of up to $10 million for information leading to their identification or location, marking the latest effort to disrupt operations of Iranian cyber operatives that has caused significant financial damage and operational disruption across multiple sectors including news, shipping, travel, energy, financial services, and telecommunications throughout the United States, Europe, and the Middle East. Shirinkar oversees the Shahid Shushtari group, previously identified under multiple cover names including Aria Sepehr Ayandehsazan, Emennet Pasargad, Eeleyanet Gostar, and Net Peygard Samavat Company. Whereas, Sedighian serves as a long-time employee working closely with Shirinkar in planning and conducting cyber operations on behalf of Iran’s IRGCs Cyber-Electronic Command, the State Department said. In August 2020, Shahid Shushtari actors began a multi-faceted campaign targeting the US presidential election, combining computer intrusion activity with exaggerated claims of access to victim networks to enhance psychological effects. The US Treasury Department designated Shahid Shushtari and six employees on November 18, 2021, pursuant to Executive Order 13848 for attempting to influence the 2020 election. Read: Six Iranian Hackers Identified in Cyberattacks on US Water Utilities, $10 Million Reward Announced The Infrastructure and Olympic Targeting Since 2023, Shahid Shushtari established fictitious hosting resellers named “Server-Speed” and “VPS-Agent” to provision operational server infrastructure while providing plausible deniability. These resellers procured server space from Europe-based providers including Lithuania’s BAcloud and UK-based Stark Industries Solutions. In July 2024, actors used VPS-Agent infrastructure to compromise a French commercial dynamic display provider, attempting to display photo montages denouncing Israeli athletes’ participation in the 2024 Olympics. This cyberattack was coupled with disinformation including fake news articles and threat messages to Israeli athletes under the banner of a fake French far-right group. Following the October 7, 2023, Hamas attack, Shahid Shushtari used cover personas including “Contact-HSTG” to contact family members of Israeli hostages, attempting to inflict psychological trauma. The group also undertook significant efforts to enumerate and obtain content from IP cameras in Israel, making images available via several servers. AI Integration and Hack-and-Leak Operations Shahid Shushtari incorporated artificial intelligence into operations, including AI-generated news anchors in the “For-Humanity” operation that impacted a US-based Internet Protocol Television streaming company in December 2023. The group leverages AI services including Remini AI Photo Enhancer, Voicemod, Murf AI for voice modulation, and Appy Pie for image generation, a joint October advisory from the U.S. and Israeli agencies stated. Since April 2024, the group used the online persona “Cyber Court” to promote activities of cover-hacktivist groups including “Makhlab al-Nasr,” “NET Hunter,” “Emirate Students Movement,” and “Zeus is Talking,” conducting malicious activity protesting the Israel-Hamas conflict. FBI assessments indicate these hack-and-leak operations are intended to undermine public confidence in victim network security, embarrass companies and targeted countries through financial losses and reputational damage. Anyone with information on Mohammad Bagher Shirinkar, Fatemeh Sedighian Kashi, or Shahid Shushtari should contact Rewards for Justice through its secure Tor-based tips-reporting channel.
- MI5 Issues Spy Alert as Chinese Intelligence Targets UK Parliament Through LinkedInby Mihir Bagwe on November 19, 2025 at 11:12 am
Two headhunters named Amanda Qiu and Shirly Shen appeared on LinkedIn offering lucrative freelance work authoring geopolitical consultancy reports, but MI5 now confirms they served as fronts for China’s Ministry of State Security conducting recruitment operations targeting British parliamentarians, staffers, and officials with access to sensitive government information. On Tuesday, Britain’s domestic intelligence service issued an espionage alert to MPs, Peers, and Parliamentary staff warning that Chinese intelligence officers are attempting to recruit individuals through professional networking sites in what Security Minister Dan Jarvis characterized as a “covert and calculated attempt by China to interfere with our sovereign affairs”. House of Commons Speaker Lindsay Hoyle circulated the MI5 alert warning that Chinese state actors were “relentless” in their efforts to interfere with parliamentary processes and influence activity at Westminster. The alert named two specific LinkedIn profiles believed to be conducting outreach at scale on behalf of Beijing’s intelligence apparatus. Social Engineering Route MI5 assessed that the Ministry of State Security was using websites like LinkedIn to build relationships with parliamentarians to collect sensitive information on the UK for strategic advantage. The fake headhunter profiles offered consulting opportunities while actually intending to lay groundwork for long-term relationships that could be exploited for intelligence collection. Security Minister Jarvis told Parliament that targets extended beyond parliamentary staff to include economists, think tank consultants, and government officials. “This government’s first duty is to keep the country safe, which is why I’ve announced new action to give security officials the powers and tools they need to help disrupt and deter foreign espionage activity wherever they find it,” Jarvis stated. The minister said the espionage alerts represent one of the main tools used to undermine spies’ ability to operate, with the public exposure intended to disrupt ongoing recruitment operations and warn potential targets. Pattern of Hostile Activity Jarvis noted the LinkedIn recruitment attempts build on a pattern of hostile activity from China, citing Beijing-linked actors targeting parliamentary emails in 2021 and attempted foreign interference activity by Christine Lee in 2022. Lee, a London-based lawyer, was accused by MI5 of facilitating covert donations to British parties and legislators on behalf of foreign nationals coordinating with the Chinese Communist Party’s United Front Work Department. The alert arrives weeks after prosecutors abruptly abandoned a case against two British men charged with spying on MPs for Beijing. Christopher Cash, a former parliamentary researcher, and Christopher Berry, an academic, faced charges under the Official Secrets Act 1911 but prosecutors claimed the government’s evidence was missing a critical element. That critical element was the government’s refusal to call China an “enemy” or “national security threat,” which prosecutors said meant they had no option but to collapse the case since the 1911 Act requires information passed on to be useful to an enemy. New Counter-Espionage Action Plan The government announced a comprehensive Counter Political Interference and Espionage Action Plan to disrupt and deter state-sponsored spying. Intelligence services will deliver security briefings for political parties and issue new guidance to election candidates helping them recognize, resist, and report suspicious activity. Authorities will work with professional networking sites to make them more hostile operating environments for spies, while new Elections Bill provisions will tighten rules on political donations. Jarvis added the government will continue taking further action against China-based actors involved in malicious cyber activity against the UK and allies. The government committed £170 million to renew sovereign and encrypted technology that civil servants use to safeguard sensitive work. An additional £130 million will fund projects including building Counter Terrorism Policing’s ability to enforce the National Security Act and supporting the National Cyber Security Centre’s work with critical businesses to protect intellectual property. Jarvis also informed Parliament that the government completed removal of surveillance equipment manufactured by companies subject to China’s National Intelligence Law from all sensitive sites operated worldwide by the British government. “As a country with a long and proud history of trading around the world, it’s in our interests to continue to seek an economic relationship with China, but this government will always challenge countries whenever they undermine our democratic way of life,” Jarvis declared. The National Security Act provides government power to prosecute those engaging in espionage activity, with offenses including obtaining protected information, assisting a foreign intelligence service, and obtaining material benefit from a foreign intelligence service. The government recently introduced the Cyber Security and Resilience Bill to help protect organizations from cyber threats posed by states like China. Also read: ENISA and European Commission Launch €36 Million EU Cybersecurity Reserve to Strengthen Digital Resilience
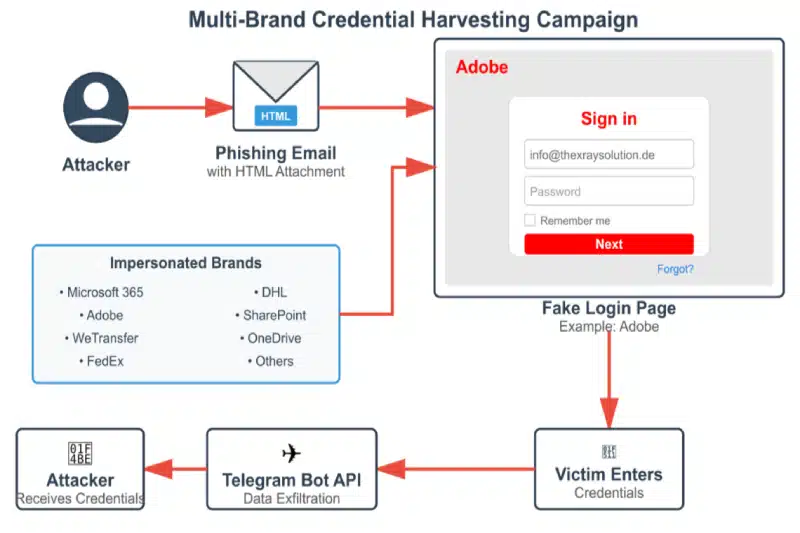
- Cyble Detects Phishing Campaign Using Telegram Bots to Siphon Corporate Credentialsby Mihir Bagwe on November 11, 2025 at 6:53 pm
Cybersecurity researchers at Cyble have uncovered an extensive phishing campaign that represents a significant evolution in credential theft tactics. The operation, which targets organizations across multiple industries in Central and Eastern Europe, bypasses conventional email security measures by using HTML attachments that require no external hosting infrastructure. Unlike traditional phishing attacks that rely on suspicious URLs or compromised servers, this campaign embeds malicious JavaScript directly within seemingly legitimate business documents. When victims open these HTML attachments—disguised as requests for quotation (RFQ) or invoices—they’re presented with convincing login interfaces impersonating trusted brands like Adobe, Microsoft, FedEx, and DHL. How the Attack Works The attack chain begins with targeted emails posing as routine business correspondence. The HTML attachments use RFC-compliant filenames such as “RFQ_4460-INQUIRY.HTML” to appear legitimate and avoid triggering basic security filters. Attack Flow (Source: Cyble) Once opened, the file displays a blurred background image of an invoice or document with a centered login modal, typically branded with Adobe styling. The victim, believing they need to authenticate to view the document, enters their email and password credentials. Behind the scenes, embedded JavaScript captures this data and immediately transmits it to attacker-controlled Telegram bots via the Telegram Bot API. This approach eliminates the need for traditional command-and-control infrastructure, making the operation harder to detect and disrupt. “The sophistication lies not just in the technical execution but in how it circumvents multiple layers of security,” explains the Cyble Research and Intelligence Labs (CRIL) team. The self-contained nature of the HTML files means they don’t trigger alerts for suspicious external connections during initial email scanning. Technical Sophistication Analysis of multiple samples reveals ongoing development and refinement of the attack methodology. Earlier versions used basic JavaScript, while more recent samples implement CryptoJS AES encryption for obfuscation and sophisticated anti-forensics measures. Advanced samples block common investigation techniques by disabling F12 developer tools, preventing right-click context menus, blocking text selection, and intercepting keyboard shortcuts like Ctrl+U (view source) and Ctrl+Shift+I (inspect element). These measures significantly complicate analysis efforts by security researchers and forensic investigators. The malware also employs dual-capture mechanisms, forcing victims to enter their credentials multiple times while displaying fake “invalid login” error messages. This ensures accuracy of the stolen data while maintaining the illusion of a legitimate authentication failure. Beyond credentials, the samples collect additional intelligence including victim IP addresses (using services like api.ipify.org), user agent strings, and other environmental data that could be valuable for subsequent attacks. Scale and Targeting CRIL’s investigation identified multiple active Telegram bots with naming conventions like “garclogtools_bot,” “v8one_bot,” and “dollsman_bot,” each operated by distinct threat actors or groups. The decentralized infrastructure suggests either collaboration among multiple cybercriminal groups or widespread availability of phishing toolkit generators. The campaign primarily targets organizations in the Czech Republic, Slovakia, Hungary, and Germany, with affected industries including manufacturing, automotive, government agencies, energy utilities, telecommunications, and professional services. The geographic concentration and industry selection indicate careful reconnaissance and targeting based on regional business practices. Threat actors customize their approach for different markets, using German-language variants for Telekom Deutschland impersonation and Spanish-language templates for other targets. The modular template system enables rapid deployment of new brand variants as the campaign evolves. Detection and Defense Security teams face challenges in detecting this threat due to its innovative use of legitimate platforms. Traditional indicators like suspicious URLs or known malicious domains don’t apply when the attack infrastructure consists of HTML attachments and Telegram’s legitimate API. Cyble recommends organizations implement several defensive measures. Security operations centers should monitor for unusual connections to api.telegram.org from end-user devices, particularly POST requests that wouldn’t occur in normal business operations. Network traffic to third-party services like api.ipify.org and ip-api.com from endpoints should also trigger investigation. Email security policies should treat HTML attachments as high-risk file types requiring additional scrutiny. Organizations should implement content inspection that flags HTML attachments containing references to the Telegram Bot API or similar public messaging platforms. For end users, the guidance remains straightforward: exercise extreme caution with unsolicited HTML attachments, especially those prompting credential entry to view documents. Any unexpected authentication request should be verified through independent channels before entering credentials. Cyble has published complete indicators of compromise, including specific bot tokens, attachment patterns, and YARA detection rules to its GitHub repository, enabling security teams to hunt for signs of compromise within their environments and implement preventive controls. Also read: Over 20 Malicious Crypto Wallet Apps Found on Google Play, CRIL Warns
- Chinese Hackers Impersonate U.S. Congressman in Malware Sting on Trade Stakeholders: Reportby Mihir Bagwe on September 8, 2025 at 9:37 am
Chinese hackers, allegedly linked to the state, attempted to infiltrate the U.S. networks during sensitive trade discussions earlier this year by impersonating a sitting congressman, according to a report in The Wall Street Journal. In July, as Washington and Beijing prepared for high-level trade negotiations in Sweden, targeted emails were sent to American trade groups, law firms, and federal agencies. The messages, appearing to come from Representative John Moolenaar — chairman of the House committee on U.S.–China strategic competition — urged recipients to review draft sanctions legislation. The attachment, however, contained spyware, the Journal reported. Investigators later attributed the activity to APT41, a hacking group long suspected of ties to China’s Ministry of State Security. Cyber analysts told the Journal that if opened, the attachment could have given attackers deep access to victim systems, enabling them to extract sensitive documents and monitor ongoing negotiations. The FBI confirmed it was investigating. “We are working with our partners to identify and pursue those responsible,” an FBI spokesperson told the newspaper. Capitol Police declined to comment. Moolenaar condemned the operation, calling it “another example of China’s offensive cyber operations designed to steal American strategy and leverage it.” He added, “We will not be intimidated.” Beijing rejected the allegations, with a Chinese Embassy statement insisting that the country “firmly opposes and combats all forms of cyber attacks and cyber crime” and warning against “smearing others without solid evidence.” APT41’s Technical Playbook APT41, also tracked under aliases such as Double Dragon and Barium, is one of China’s most versatile state-sponsored groups. Analysts told the Journal that the group’s hallmark is its dual-use capability — conducting espionage on behalf of the state while also engaging in financially motivated cybercrime. The group has a long history of using spear-phishing and watering-hole attacks, often impersonating trusted figures or exploiting zero-day vulnerabilities. Its malware arsenal includes ShadowPad, a modular backdoor frequently used in Chinese espionage campaigns, and other custom loaders designed to maintain persistence. Also read: Chinese Hackers Targeted Taiwanese Research Institute with ShadowPad and Cobalt Strike APT41 also makes heavy use of publicly available exploits. Past alerts from U.S. agencies note the group’s exploitation of vulnerabilities in Citrix, Atlassian Confluence, and Microsoft Exchange. Analysts believe the spyware used in the Moolenaar impersonation likely followed a familiar playbook: reconnaissance, credential harvesting, lateral movement, and long-term surveillance. A Track Record of Global Intrusions The campaign described by the Journal is not an isolated incident. In 2020, the U.S. Department of Justice indicted five Chinese nationals linked to APT41 on charges of hacking more than 100 companies worldwide. Victims included software firms, universities, telecom providers, and even non-profit organizations. Prosecutors alleged the group stole source code, proprietary business information, and intellectual property on a massive scale. Beyond espionage, APT41 has been tied to cybercrime for profit. Researchers have documented its role in stealing digital gaming currency and selling access to compromised servers. The group’s ability to switch seamlessly between state-directed intelligence operations and financially motivated crime sets it apart from many other advanced persistent threat (APT) groups. More recently, APT41 has been implicated in targeting the healthcare sector, with reports of attempted intrusions into hospitals and pharmaceutical firms during the COVID-19 pandemic. Security analysts say such activity aligns with Beijing’s interest in gaining access to sensitive medical research and health data. Espionage Pattern The phishing campaign took place just days before negotiators agreed to extend a tariff truce and resume discussions on a possible summit between President Trump and Chinese President Xi Jinping. Experts noted that compromising advisory groups or law firms tied to the talks would allow Beijing to anticipate U.S. positions and adjust its strategy. Mandiant told the Journal that the spyware in this case could have burrowed deep into networks, enabling long-term monitoring. For adversaries like APT41, analysts said, such access is more valuable than short-term disruption — it provides leverage in negotiations and insights into political decision-making. Earlier this year, hackers impersonated Secretary of State Marco Rubio using AI-generated content, while phishing attempts targeted White House staff, including Chief of Staff Susie Wiles, the Journal reported. Together, these incidents point to an intensifying focus on U.S. political leadership and policy processes. The attempt to compromise U.S. trade stakeholders shows how cyber operations increasingly run parallel to geopolitical negotiations. Experts said that while military maneuvers often capture headlines, cyber espionage has become a quieter but equally potent front. As tensions over technology, tariffs, and national security continue to define U.S.–China relations, espionage campaigns exploiting trust, urgency, and political credibility are likely to remain central to Beijing’s toolkit.
- Czechia Warns of Chinese Data Transfers and Remote Administration for Espionageby Mihir Bagwe on September 5, 2025 at 8:26 am
Czechia’s national cybersecurity watchdog has issued a warning about foreign cyber operations, focussed on Chinese data transfers and remote administration, urging both government bodies and private businesses to bolster defenses amid rising espionage campaigns tied to China and Russia. The alert, published this week by the National Cyber and Information Security Agency (NÚKIB), cites ongoing risks to government systems, energy providers, telecoms, and other critical infrastructure operators. While NÚKIB did not name specific incidents in its bulletin, the agency said that “selected foreign states” were increasingly engaged in long-term campaigns designed to compromise strategic sectors, exfiltrate sensitive information, and undermine public trust. The Core Threat Assessment NÚKIB has classified the threat as “High – likely to very likely,” encompassing two primary concerns; data transfers to the People’s Republic of China (PRC) and its Special Administrative Regions (Hong Kong and Macau), and remote administration of technical assets from these territories. This assessment applies to all entities regulated under Czech cybersecurity legislation, including critical infrastructure operators. The agency’s decision to issue this warning stems from what it describes as “facts established during the exercise of its powers, supplemented by unclassified and classified information obtained from domestic and foreign partners.” At the heart of NÚKIB’s warning lies a detailed analysis of China’s legal environment, which the agency argues fundamentally compromises data security. The assessment identifies several problematic regulations: National Security Framework: The 2015 National Security Law imposes broad obligations on Chinese citizens and organizations to assist state authorities in matters of national security. More significantly, the 2017 National Intelligence Law requires “every citizen and organisation” to support intelligence activities and maintain confidentiality. Corporate Control Mechanisms: The 2013 Company Law mandates Communist Party of China (CPC) organizations within companies, effectively allowing party influence over corporate operations. This creates a direct channel for state interference in nominally private enterprises. Vulnerability Reporting Requirements: 2021 regulations require technology manufacturers to report security vulnerabilities to the Ministry of Industry and IT within two days, with subsequent reporting to the Ministry of State Security. Crucially, manufacturers are prohibited from disclosing these vulnerabilities to foreign organizations. The Counter-Espionage Law, particularly following its 2023 amendment, expands espionage definitions to encompass virtually any documents or data deemed related to national security by Chinese authorities. This creates an environment where state access to private data is not only legal but mandated. Special Administrative Regions, Means Extended Reach NÚKIB’s analysis extends to Hong Kong and Macau, territories that maintain economic autonomy while remaining under Chinese sovereignty. The agency identifies concerning legislation in both regions The 2024 Safeguarding National Security Ordinance integrates China’s national security framework into Hong Kong’s legal system, creating vague definitions of “state secrets” that could encompass economic, social, technological, or scientific activities. In Macau, the 2019 Cybersecurity Law grants the Cybersecurity Incident Alert and Response Center (CARIC) authority to conduct real-time monitoring of critical infrastructure data transmissions, with no supervisory mechanism to prevent abuse. Attribution and Active Threats The warning gains particular weight from recent attribution activities. In May, the Czech government publicly attributed cyberattacks against its Ministry of Foreign Affairs to APT31, a group associated with China’s Ministry of State Security. This campaign, active since 2022, targeted critical infrastructure and demonstrated sophisticated, persistent capabilities. The Czech government “strongly condemns this malicious cyber campaign against its critical infrastructure” and noted that “such behavior undermines the credibility of the People´s Republic of China and contradicts its public declarations. This attribution wasn’t conducted in isolation. NÚKIB worked alongside the Security Information Service, Military Intelligence, and the Office for Foreign Relations and Information to achieve what they describe as “a high degree of certainty about the responsible actor.” The Czech warning aligns with broader international concerns about Chinese technology risks. NÚKIB notes that Italy, Germany, the Netherlands, and Australia have taken measures regarding specific Chinese products and services, while the Five Eyes intelligence alliance has issued advisories about Chinese cyber espionage groups. Also read: Six Australian MPs Confirm They were Targeted by China’s APT31 Hackers The agency specifically references a 2021 European Data Protection Board study concluding that Chinese laws allow “broad access by PRC state authorities to data without sufficient independent oversight,” fundamentally contradicting GDPR principles of transparency, proportionality, and legal protection. Critical Infrastructure Implications The warning carries particular significance for critical infrastructure operators. NÚKIB emphasizes that disruption of availability, confidentiality, or integrity of backbone systems “could potentially have a significant impact on many people in the territory of the Czech Republic.” The agency identifies specific technology categories of concern: Personal devices (smartphones, watches, electric vehicles) Cloud services Photovoltaic inverters IP cameras Health technology Smart meters A Pattern of Firm Stances The warning follows a series of steps by the Czech government to push back against foreign digital influence. Earlier this year, Prague moved to restrict the use of Chinese-developed AI platforms such as DeepSeek, citing risks of data exfiltration and systemic manipulation. The Ministry of Foreign Affairs said at the time that trust in the country’s digital infrastructure was “not compatible with applications subject to extraterritorial control by foreign powers.” This builds on years of concern over technology supply chains. Czechia was one of the first EU members to limit Huawei and ZTE equipment in its 5G rollout, a decision backed by NÚKIB in 2018 that placed it firmly in the transatlantic camp on telecom security. The latest warning suggests the government is prepared to extend that logic into AI systems and cloud-based platforms as well. The warning reflects evolving geopolitical realities. NÚKIB notes that China’s support for Russia in the Ukraine conflict has intensified its interest in European affairs, manifesting in increased cyber espionage activities. The agency cites intelligence assessments showing Chinese actors targeting Czech state institutions with increasingly sophisticated spear-phishing attacks. The Security Information Service has repeatedly emphasized technological dependence on China as a strategic vulnerability, particularly given China’s “autocratic regime with global ambitions to create an effective counterbalance to the G7 countries.
- Not Larger Telecommunications, But Smaller Dutch ISPs Also Targeted in Broader Salt Typhoon Campaignby Mihir Bagwe on August 29, 2025 at 1:51 pm
China-linked espionage actor Salt Typhoon is again in news but this time not for targeting larger telecommunication giants, instead its the smaller internet and hosting service providers in the Netherlands. The Dutch intelligence service on Thursday said that the country “didn’t receive the same level of attention from the Salt Typhoon hackers as those in the U.S.,” but it “can now corroborate some of the findings of the U.S. investigation with independent intelligence.” The Dutch MIVD and AIVD (General Intelligence and Security Service) said, “The Chinese hacker group had access to routers belonging to the Dutch targets. As far as we know, the hackers did not penetrate any further into their internal networks.” No information on the number of routers accessed or which sectors were targeted was provided but the authorities said, “(It)did observe targets in the Netherlands. These were not large telecommunications providers, but smaller internet service and hosting providers.” The MIVD and the AIVD have been warning for some time about the growing Chinese cyber threat,” the authorities said. “These activities have become so sophisticated that continuous effort and attention are required to promptly detect and mitigate cyber operations against Dutch interests. This can reduce risks, but not eliminate them entirely. This poses a major challenge to Dutch resilience.” The MIVD, AIVD, and the National Cyber Security Centre (NCSC) have previously shared threat intelligence with targets and other relevant audiences, whenever possible. Salt Typhoon Campaign’s Roots This announcement cam on the heels of a multi-nation joint advisory released a day before that warned of China-linked threat groups Salt Typhoon and GhostEmperor’s targeting of critical infrastructure networks around the world in a persistent campaign of cyber espionage. Read: Chinese State Hackers Target Global Critical Infrastructure, NSA Warns These operations have been traced to three China-based companies: Sichuan Juxinhe Network Technology Co. Ltd., Beijing Huanyu Tianqiong Information Technology Co., Ltd., and Sichuan Zhixin Ruijie Network Technology Co., Ltd., which allegedly act as a front for the Chinese Ministry of State Security and the People’s Liberation Army. Salt Typhoon’s wider operation net first came to light late last year when several U.S. Telecom companies reported hack and wiretap of key members of the Presidential elections. In an official hearing, earlier this year, the chairman of the Senate Intelligence Committee said, evicting these intruders will require replacing “thousands and thousands and thousands” of network devices. Read: China Attack on U.S. Telecom Networks: ‘Thousands and Thousands’ of Devices Need to Be Replaced The Salt Typhoon tied breach of U.S. telecom networks lasted for more than a year in some cases, and while only 150 victims were notified at the time, the total could eventually number in the “millions,” experts had warned Warner, a former telecom venture capitalist, called the breaches the “worst telecom hack” in the nation’s history – by far.
- China-Linked Espionage Campaign Hijacks Web Traffic to Target Diplomatsby Mihir Bagwe on August 26, 2025 at 9:32 am
Google’s Threat Intelligence Group has uncovered a cyber espionage campaign of a PRC-linked threat actor, which it tracks as UNC6384, using captive portals and adversary-in-the-middle tactics to target diplomats across Southeast Asia. Captive portals are the type of sign-in pages familiar to anyone who has logged into hotel Wi-Fi. Instead of leading to a legitimate login, these portals mimicked VPN services or software update pages to deceive victims. Once a victim visited, they were served a digitally signed downloader tracked as STATICPLUGIN, which in turn deployed SOGU.SEC, a variant of the notorious PlugX backdoor. PlugX has long been associated with Chinese state-backed intrusion playbook. But this latest variant was delivered through an updated tradecraft designed to avoid detection. Technical Details Delivery Mechanism: The malware was signed with a legitimate digital certificate, allowing it to bypass endpoint defenses. Execution Techniques: UNC6384 used indirect execution and adversary-in-the-middle (AitM) techniques to blend with normal traffic and avoid signature-based detection. Data Collection: Once inside, SOGU.SEC enabled lateral movement, file exfiltration, and ongoing surveillance of sensitive diplomatic systems. Infrastructure: The group operated attacker-controlled redirectors, which intercepted traffic and funneled it through malicious portals. Attack Chain (Image Credit: Google Threat Intelligence Group) Google said it notified the compromised organizations via government-backed alerts and sharing malicious domains and file hashes that were also added to its Safe Browsing feature. Why Diplomats? UNC6384’s targeting of diplomats has the geopolitical underpinnings of the campaign. The group zeroed in on government agencies, embassies and foreign service workers operating in Southeast Asia—an area where China has pressing economic and strategic interests. Unlike ransomware or financially motivated operations, this activity reflects the calculated objectives of a nation-state adversary. Diplomats are high-value strategic targets. By embedding themselves in their systems, attackers can gain insight into negotiations, policy positions, and alliances. According to recent analysis, Chinese APT groups are increasingly focusing on strategic pre-positioning in critical infrastructure and supply chains, often leveraging edge devices, software frameworks with minimal endpoint defenses, and “living-off-the-land” techniques to ensure persistence and stealth. Also read: ‘UNC3886 is Attacking Our Critical Infrastructure Right Now’: Singapore’s National Security Lawmaker
- Russia’s FSB-Linked Hackers Targeting Cisco Network Gear Used in Critical Infrastructureby Mihir Bagwe on August 21, 2025 at 7:14 am
How often do you hear people talking about issues of legacy systems—especially in critical infrastructure environments? Here’s another example of how deeply rooted this issue is—legacy Cisco router infrastructure remains a Russian intelligence vault. A new alert from the FBI and a detailed analysis from Cisco Talos reveal how a decade-old vulnerability, tracked as CVE-2018-0171, in Cisco’s Smart Install feature continues to fuel state-level espionage campaigns against critical infrastructure. A Legacy Weakness with Persistent Danger CISA flagged this vulnerability back in 2018, warning that Russian state-sponsored actors had exploited Cisco’s Smart Install and unencrypted management protocols like SNMP and Telnet to harvest network configurations, inject firmware, and control routers for intelligence collection and lateral exploitation. That advisory revealed how unsecured GRE tunnels, SNMP, and TFTP were easy pathways for attackers to extract configuration files and password hashes from enterprise and SOHO devices. This compromised network infrastructure could be weaponized for traffic interception or even destructive operations, CISA had warned, at the time. Fast forward to the latest advisory and these are no longer just theoretical risks. The tools and techniques of SNMP abuse, misconfigured routers, use of TFTP over UDP, still enable attackers to extract device configurations, carve network maps and enact persistent access with minimal visibility. Also read: Urgent: CISA Flags Cisco Device Risks, Weak Passwords a Major Threat Static Tundra’s Stealthy Campaign, Decade in the Making Cisco Talos has now dubbed the threat actor exploiting this weakness as Static Tundra, a Russian-linked espionage group likely tied to FSB’s Center 16, also known as Energetic Bear. Talos assesses with high confidence that Static Tundra has spent years infiltrating unpatched or end-of-life Cisco network devices, particularly those with Smart Install enabled, and has done so across telecoms, higher education institutes and manufacturing in multiple continents. Their techniques include: Exploiting CVE-2018-0171 to inject a TFTP-based fallback, retrieving startup configurations. Abusing SNMP, occasionally via spoofed source addresses, to retrieve credentials and enable remote access. Deploying the notorious SYNful Knock firmware implant to maintain stealth and resilience through reboots. Leveraging GRE tunnels and NetFlow collection to quietly exfiltrate traffic and intelligible metadata. Talos notes the group operates with precision, picking targets aligned with shifting geopolitical priorities—particularly during the Ukraine conflict escalation. What’s more worrying is that the researchers observed many compromised devices remain infected as organizations still fail to patch or disable Smart Install feature, despite patches being available since 2018. Real-World Risk Across Sectors and Borders The combined findings show that the threat persists because of structural neglect. Unpatched firmware, enabled legacy features, and unmanaged network gear are the primary reasons. While CISA’s 2018 warning outlined the risk, Talos confirms that attackers continue to harvest sensitive configuration data, creating long-term espionage footholds. Sophisticated threat actors controlling key network infrastructure can manipulate traffic flows, enable command-and-control for hidden implants, and pivot laterally—transforming compromised routers into control hubs for broader attacks, cyber experts warned. A Non-Negotiable Security Imperative The risk as we said earlier isn’t hypothetical anymore. It’s ongoing and systemic. Here are some foundational steps every enterprise and critical infrastructure network must take, as per Talos researchers: Patch or disable Smart Install immediately—CVE-2018-0171 remains widely exploitable. Encrypt management channels, disable legacy protocols, harden SNMP and AAA policies. Profile router behavior via NetFlow, log monitoring, and IDS signature deployment. Maintain accurate device inventories and restrict remote access to critical appliances. Static Tundra’s campaigns make clear that network devices are not passive infrastructure. They are prime asymmetric targets. The vulnerability in Smart Install isn’t new, but the threat remains potent. Critical infrastructure operators need to harden network gear, build detection-first strategies, and elevate device security to boardroom-level concern.