- How ‘digital twins’ could help prevent cyber-attacks on the food industryby Sabah Suhail, Research Fellow, School of Electronics, Electrical Engineering and Computer Science, Queen’s University Belfast on November 27, 2025 at 1:32 pm
Digital twins allow organisations to simulate real-time events.
- An AI lab says Chinese-backed bots are running cyber espionage attacks. Experts have questionsby Toby Murray, Professor of Cybersecurity, School of Computing and Information Systems, The University of Melbourne on November 17, 2025 at 3:57 am
Anthropic says its Claude Code tool was used in a sophisticated, automated campaign to steal sensitive information.
- The threat of sabotage from China is growing. That’s not an excuse to erode Australians’ freedomsby Ihsan Yilmaz, Deputy Directory (Research Development), Deakin Institute for Citizenship and Globalisation & Research Professor of Political Science and International Relations, Deakin University on November 14, 2025 at 12:44 am
There’s a risk of a slide towards digital authoritarianism as Australia responds to these growing threats.
- ‘High-impact sabotage’: spy chief issues grave warning about espionage and sabotage threatby Sarah Kendall, Adjunct Research Fellow, The University of Queensland; Griffith University on November 13, 2025 at 12:33 am
The head of ASIO says authoritarian regimes are more willing to disrupt critical infrastructure to damage the economy and sow social discord.
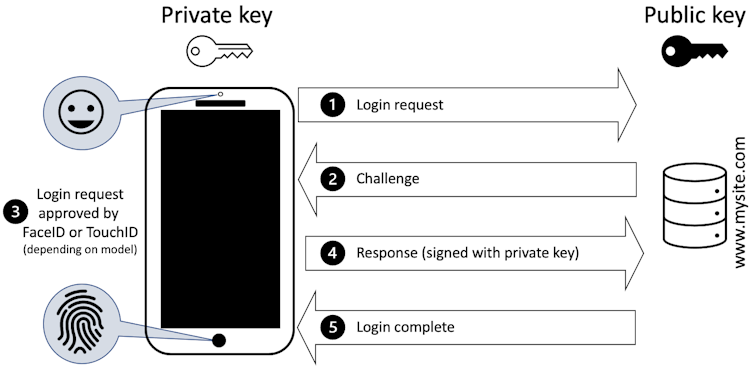
- What’s the difference between passwords and passkeys? It’s not just the protection they provideby Paul Haskell-Dowland, Professor of Cyber Security Practice, Edith Cowan University on October 23, 2025 at 11:31 pm
Passkeys are stronger than passwords by design. But they have other benefits too.
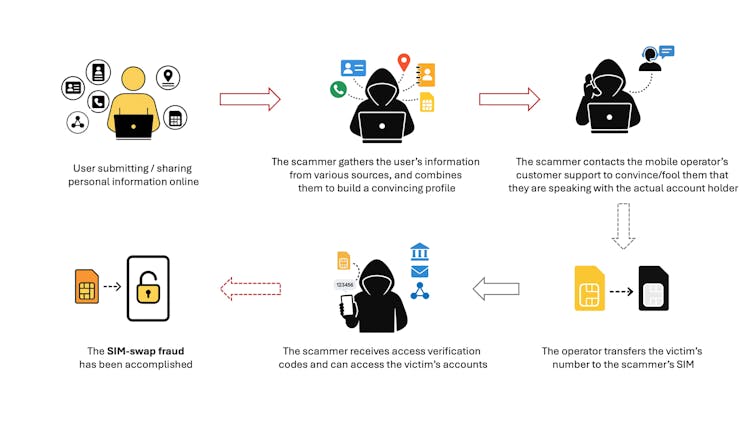
- M&S cyberattacks used a little-known but dangerous technique – and anyone could be vulnerableby Hossein Abroshan, Senior Lecturer, School of Computing and Information Science, Anglia Ruskin University on May 14, 2025 at 3:09 pm
Sim-swap fraud is becoming increasingly prevalent.
- Major cybercrime crackdowns signal shift in global cybersecurity strategiesby Christine Abdalla Mikhaeil, Assistant professor in information systems, IÉSEG School of Management on November 24, 2024 at 2:32 pm
International law enforcement efforts against ransomware groups achieved successes in 2024. More global coordination is needed to keep up with cybercriminals, who are constantly adapting.
- The dangers of voice cloning and how to combat itby Leo S.F. Lin, Senior Lecturer in Policing Studies, Charles Sturt University on October 9, 2024 at 6:58 pm
In just seconds, scammers can clone a voice and use it to extort people. What can be done to safeguard against the threat?
- As an ethical hacker, I can’t believe the risks people routinely take when they access the internet in publicby Christopher Patrick Hawkins, Lecturer in Cyber Security and Computer Science, University of Staffordshire on October 8, 2024 at 4:25 pm
If you’re tempted to do a make a couple of cheeky payments while waiting for the band to come on, think again.
- Is your car a threat to national security? It can be – regardless of where it’s madeby Dennis B. Desmond, Lecturer, Cyberintelligence and Cybercrime Investigations, University of the Sunshine Coast on October 2, 2024 at 3:03 am
Modern cars made in most countries have remote control and online data features. What matters is who can access that data – and the vehicle itself.
- How to avoid being hacked: start by upping your password game – ‘12345’ doesn’t cut itby Thembekile Olivia Mayayise, Senior Lecturer, University of the Witwatersrand on June 16, 2024 at 10:41 am
The question has shifted from whether cyberattacks will occur to when and how they will happen.
- China turns to private hackers as it cracks down on online activists on Tiananmen Square anniversaryby Christopher K. Tong, Associate Professor of Asian Studies, University of Maryland, Baltimore County on May 31, 2024 at 1:02 pm
Beijing’s cyber operations are largely conducted in the shadows. But a recent leak has shed light on how the state is working with private companies to target online activism.
- MediSecure data breach: why is health data so lucrative for hackers?by Megan Prictor, Senior Lecturer in Law, The University of Melbourne on May 20, 2024 at 5:23 am
We don’t know much about the nature of this large-scale ransomware attack. But it’s not entirely surprising – health data is a prime target for cybercrime.
- What is credential stuffing and how can I protect myself? A cybersecurity researcher explainsby David Tuffley, Senior Lecturer in Applied Ethics & CyberSecurity, Griffith University on January 18, 2024 at 3:32 am
In what is colourfully termed a ‘brute force’ attack, hackers use bots to test millions of username and password combinations on different websites – until they find a match.
- What is LockBit, the cybercrime gang hacking some of the world’s largest organisations?by Jennifer Medbury, Lecturer in Intelligence and Security, Edith Cowan University on November 16, 2023 at 11:59 pm
Prolific and highly profitable, LockBit provides ransomware as a service. Aspiring cybercriminals sign up to the scheme, and the group takes a cut. Here’s how it works.
- Cyber-attacks against the UK Electoral Commission reveal an ongoing threat to democracyby Joe Burton, Professor of International Security (Security and Protection Science), Lancaster University on August 15, 2023 at 3:29 pm
Securing our voting systems to defend against hacks is vital but challenging.
- The $500 million ATO fraud highlights flaws in the myGov ID system. Here’s how to keep your data safeby Rob Nicholls, Associate professor of regulation and governance, UNSW Sydney on July 27, 2023 at 2:10 am
Scammers have exploited a simple weakness in the myGov online portal to redirect hundreds of millions of dollars in tax refunds.
- Four ways criminals could use AI to target more victimsby Daniel Prince, Professor of Cyber Security, Lancaster University on June 22, 2023 at 4:04 pm
AI could allow cybercriminals to operate with greater efficiency, targeting more people at once.
- Moveit hack: attack on BBC and BA offers glimpse into the future of cybercrimeby Danny Steed, Lecturer in Cyber Security, Cranfield University on June 19, 2023 at 1:44 pm
Cybercriminals are attempting to monetise the hacking techniques used by state actors.
- Should governments ban TikTok? Can they? A cybersecurity expert explains the risks the app poses and the challenges to blocking itby Doug Jacobson, Professor of Electrical and Computer Engineering, Iowa State University on March 23, 2023 at 12:38 pm
What data privacy risk does TikTok pose, and what could the Chinese government do with data it collects? And is it even possible to ban an app?
- Dozens of US schools, universities move to ban TikTokby Nir Kshetri, Professor of Management, University of North Carolina – Greensboro on January 18, 2023 at 1:38 pm
School officials are becoming increasingly wary of TikTok amid concerns that the app poses a risk to student safety and privacy and makes the nation vulnerable to spies.
- How not to tell customers their data is at risk: the Optus approachby Edwina Luck, Senior Lecturer QUT Business School, Advertising, Marketing and Public Relations, Queensland University of Technology on September 23, 2022 at 7:27 am
Optus used press releases, and Twitter when it could have contacted its customers by text.
- ‘Liberate the tractors’: the right to repair movement that’s regaining control of our devicesby Michael Stead, Lecturer in Sustainable Design Futures, Lancaster University on August 22, 2022 at 4:00 pm
From tractors to smartphones, consumers may own their devices but the manufacturers still often hold the keys.
- Before paying a ransom, hacked companies should consider their ethics and valuesby Michael Parent, Professor, Management Information Systems, Simon Fraser University on August 17, 2022 at 6:08 pm
Cyberattacks demanding ransoms for the release of information are on the rise. To determine if they should pay, businesses need to think about how they would react in such a scenario.
- Hackathons should be renamed to avoid negative connotationsby P. Alison Paprica, Professor (adjunct) and Senior Fellow, Institute for Health Policy, Management and Evaluation, Dalla Lana School of Public Health, University of Toronto on July 18, 2022 at 1:56 pm
“Hackathons” can imply breaching security and privacy. To more accurately reflect their creative and constructive intent, they can be referred to instead as “datathons” or “code fests.”

Hacking The Conversation
We are an ethical website cyber security team and we perform security assessments to protect our clients.