- FTC is taking another look at COPPA and kids’ online privacy – and we want your insightsby lfair on January 11, 2024 at 5:52 pm
FTC is taking another look at COPPA and kids’ online privacy – and we want your insights lfair January 11, 2024 | 12:52PM FTC is taking another look at COPPA and kids’ online privacy – and we want your insights By Lesley Fair The FTC announced proposed revisions to the Children’s Online Privacy Protection Act (COPPA) Rule on December 20, 2023. The online portal to file public comments is now open and the FTC welcomes your feedback by the March 11, 2024, deadline. You’ll want to read the Notice of Proposed Rulemaking to see what’s on the table. Some of the suggested updates address changes in technology, such as limiting push notifications to kids. Others aim to clarify and streamline the COPPA Rule and strengthen data security. And still others are designed to strengthen how children’s personal information is protected online with an aim to ensure that parents – not companies – are in charge. For example, the proposal would require targeted advertising to kids to be off by default. It’s easy to let your voice be heard. Consider the questions asked in the Notice, read the proposed revisions to the COPPA Rule, and file a comment online through Regulations.gov. Simply click the SUBMIT A FORMAL COMMENT button and start typing. Don’t be put off by the word “formal.” Of course, we welcome submissions from researchers, academics, and businesses of any size, but comments don’t need to have footnotes or charts ‘n’ graphs. A critically important part of the public comment process is to listen to the practical perspectives of parents who deal with COPPA regularly. Let us know where you stand on the FTC’s proposal to strengthen the COPPA Rule. File your public comment by March 11, 2024.
- Winter Storm Elliott: How to avoid clean-up and repair scams as you get back to businessby lfair on December 29, 2022 at 7:53 pm
Winter Storm Elliott: How to avoid clean-up and repair scams as you get back to business lfair December 29, 2022 | 2:53PM Winter Storm Elliott: How to avoid clean-up and repair scams as you get back to business By Colleen Tressler Weather emergencies don’t take a winter vacation. Scammers don’t either. Just like you, they’re watching the weather reports and preparing for storms – and they’re counting on catching you unawares. Winter Storm Elliott affected the U.S. from coast to coast. The storm’s chilling effects from record cold and snow to the loss of electricity from high winds downing trees and power lines, were felt across much of the nation. If your business has been affected by Elliott or another weather event, here’s some advice for hiring a contractor or restoration company to help with clean-up and repairs: Get recommendations from people you know and trust. Ask contractors for IDs, licenses, proof of insurance, and references before paying for services. Search online for the company’s name with words like “scam” or “complaint.” Pay by credit card or check if possible, or checks – but never with cash, gift cards, or through wire transfer companies like Western Union or MoneyGram. And only pay in full after the work is done and you’re satisfied with it. Get a contract. Never rely on handshake deals. Make sure all promises are in writing and that you understand what you’re signing. To learn more about ways to prepare for, deal with, and recover from a weather emergency – at work and at home – visit ftc.gov/WeatherEmergencies. The Small Business Administration also has advice for businesses about preparing for all kinds of emergencies, and the Department of Homeland Security’s “Ready” initiative has toolkits for business in English and Spanish. If you suspect a scam, report it to the FTC at ReportFraud.ftc.gov.
- Corporate boards: Don’t underestimate your role in data security oversightby lfair on April 28, 2021 at 1:29 pm
Corporate boards: Don’t underestimate your role in data security oversight lfair April 28, 2021 | 9:29AM Corporate boards: Don’t underestimate your role in data security oversight By Jared Ho For businesses in the middle of a global pandemic, there’s no such thing as “business as usual.” The percentage of Americans working remotely has grown substantially, now reportedly up to 33% of the U.S. workforce. Accompanying that seismic shift have been increased security threats to data, with one analysis reporting that over 36 billion online records were exposed in the first half of 2020 alone. Consumers whose lives have been upended by identity theft are paying close attention to how corporations are responding. But is the typical corporate Board of Directors giving data security the attention it deserves? In addition to the significant costs to consumers, data breaches, network intrusions, and looming cyber threats can open up a firm to substantial financial costs, reputational hits, and legal liability. The FTC has continued to challenge allegedly deceptive or unfair conduct related to companies’ data security practices. A few recent examples include settlements with SkyMed International, Tapplock, and Zoom. We’re also in the process of reviewing some data security rules for industry, including the Health Breach Notification Rule and the Gramm-Leach-Bliley Safeguards Rule. Against that backdrop, it’s essential for corporate boards to do what they can to ensure that consumer and employee data is protected. The good news is that according to a recent study, 60% of directors surveyed said they plan to improve their cybersecurity oversight role over the next year. What would that look like for a typical corporation? FTC staff has five common-sense recommendations for conscientious directors. Make data security a priority. Contrary to popular belief, data security begins with the Board of Directors, not the IT Department. A corporate board that prioritizes data security can set the tone throughout an organization by instilling a culture of security, establishing strong security expectations, and breaking down internal silos to facilitate technical and strategic collaboration. While there’s no one-size-fits-all formula, here are strategies some companies have implemented to make security a priority. Build a team of stakeholders from across your organization. Despite a 2018 study that found that 89% of CEOs treat cybersecurity as an IT function, experience suggests that cyber risk management is a “whole business” issue. A sound data security program should incorporate stakeholders from business, legal, and technology departments across the company – both high-level executives and operational experts. Of course, many committees include the Chief Information Officers and the Chief Information Security Officer, but other companies promote practical synergies by also including executives who bring a different perspective to the issues – for example, the CEO, CFO, or General Counsel. A broad and diverse range of voices can provide the board with cross-cutting information about cyber risks and solutions. Establish board-level oversight. Some corporate boards delegate their cyber risk oversight duties to an audit committee. Others have a stand-alone cybersecurity committee at the board level. Irrespective of how an organization structures its cyber risk oversight duties, the key takeaway is that cyber risks should be a priority within the board room. Board-level oversight helps to ensure that cybersecurity threats, defenses, and responses have the attention of those at upper echelons and get the resources needed to do the job right. Hold regular security briefings. When it comes to security, board members need to be in the know, but research suggests many of them are out of the loop. A 2012 survey found that fewer than 40% of corporate boards regularly received reports about privacy and security risks and 26% rarely or never got that information. According to another study, only 12% of boards frequently received cyber threat briefings. A survey of public companies conducted six years later in 2018 didn’t suggest much progress. Only 37% of board members said they felt “confident” or “very confident” that their company was properly secured against cyberattack. Of course, cybersecurity isn’t a one-and-done proposition. It’s a dynamic process that requires board members to be informed, engaged, and updated. Regular briefings prepare boards to carry out their oversight responsibility, navigate the security landscape, and prioritize threats to the company. Understand the cybersecurity risks and challenges your company faces. A strong data security program starts at the top. While it might not be the board’s role to manage day-to-day security operations, it is their job to set priorities and allocate the resources necessary to ensure effective security. Board members need to talk the talk and walk the walk. They should demonstrate a sophisticated grasp of the data security challenges their company faces and act in a way that sets the tone for the entire organization. Don’t confuse legal compliance with security. In 2019, the FTC held a series of hearings on consumer protection and technology in the 21st century. One common theme was that compliance doesn’t necessarily translate into good security. Cybersecurity threats are constantly and rapidly evolving. A strong data security program should never be reduced to a “check the box” approach geared toward meeting compliance obligations and requirements. Instead, boards should ensure that their security programs are tailored to their companies’ unique needs, priorities, technology, and data. Boards should ask tough questions about whether their policies and procedures effectively address their company’s security risks and whether actual security practices effectively address the threats they face. That no-holds-barred conversation might include fundamental questions like: What kind of data are we keeping and why? And where are we keeping it? Are our policies and procedures adequate to protect our data? Are our actual security practices in line with our policies and our public-facing statements? Are our security investments and expenditures in line with our security risks and threats? It’s more than just prevention. A strong data security program ensures that a company is undertaking reasonable precautions to protect its network and consumers’ personal information from intruders. However, no data security program is perfect and no program can guarantee that a company will be protected from attack or a data breach. If nothing else, recent breaches have demonstrated the importance of both a strong data security program and a robust incident response plan. In responding to a security incident, time is often of the essence. Every minute that employees spend attempting to flag down key executives and focus their attention on what’s happened is time taken away from the critical tasks of stanching the damage to data and implementing an appropriate response. In contrast, an effective security program ensures that when it’s appropriate, a security incident can be swiftly elevated to the appropriate level. In addition, building organizational resilience into your security program can help your company sustain operations while responding to a security incident. Learn from mistakes. If your company has had the misfortune of experiencing a data breach, take the opportunity to learn from the incident and improve your program. Companies often require periodic independent third-party assessments to establish a baseline against which future progress can be measured and – in the event of a security incident – to determine how a breach occurred. Of course, learning from other companies’ mistakes can be just as valuable (and substantially less painful). There are certainly no shortage of data breaches and many likely involve competitors or other parties in similar lines of business. Boards should take the opportunity to understand the cybersecurity risks related to their industry and learn from their company’s own mistakes as well as the mistakes of others. The FTC Business Center has data security resources for companies of any size and in any sector.
- Background checks? Don’t double-dip.by lfair on February 16, 2017 at 2:56 pm
Background checks? Don’t double-dip. lfair February 16, 2017 | 9:56AM Background checks? Don’t double-dip. By Tiffany George Need to verify an applicant’s employment or income history? Checking to see if a candidate has a criminal history or civil judgments? If you get information from a company that compiles it so you can make eligibility determinations, you must comply with the Fair Credit Reporting Act (FCRA). That means no double-dipping. If you get a consumer report for one purpose, don’t use it for a different purpose. The FCRA applies when you use consumer reports to determine things like eligibility or pricing for credit, insurance, or housing; eligibility for employment, government benefits, licenses, membership in an organization; or admission to an educational institution. If you use consumer reports to make eligibility decisions, make sure you review the Notice to Users of Consumer Reports. Consumer reporting agencies (CRAs) are required to give you this document to inform you of your obligations under the FCRA. Other federal or local laws also may apply to your use of consumer reports. When you get a consumer report, you must certify to the CRA the purpose for which you will use it. You must use the report only for that purpose. For example, that means if you get a report for a membership determination, you can’t then use it to make a credit decision. Or if you get a report to determine eligibility for a government benefit, you can’t then give it to a different government agency to make another eligibility determination. Why is this important? When consumers request copies of their files, CRAs must inform them about who has obtained reports on them. This helps consumers track each organization that has used a consumer report to make an eligibility decision about them. Getting a new consumer report when you have a new purpose helps your business ensure that you obtain the most current information about the consumer. When using consumer reports, here are a few more FCRA principles to keep in mind: If you make a negative decision about a person based on a consumer report, you must provide the person with notice of the decision – an “adverse action notice” including the name, address, and phone number of the CRA that prepared the report, a statement that the CRA did not make the decision and is not able to provide the reasons for the adverse action, and that the person has a right to receive a free copy of the report within 60 days and dispute inaccurate information. The adverse action notice may be provided orally, electronically, or in writing. A written adverse action notice is best because it provides proof of compliance. The CRA that provided you with the consumer report may have a model adverse action notice. Finished with the report? Once you no longer need it, you must securely dispose of the report and any information gathered from it.
- FTC’s Lord & Taylor case: In native advertising, clear disclosure is always in styleby lfair on March 15, 2016 at 12:37 pm
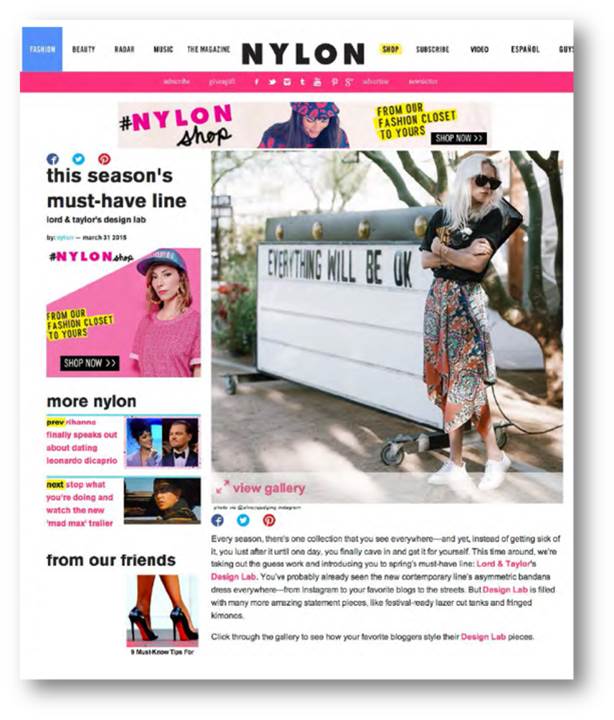
FTC’s Lord & Taylor case: In native advertising, clear disclosure is always in style lfair March 15, 2016 | 8:37AM FTC’s Lord & Taylor case: In native advertising, clear disclosure is always in style By Lesley Fair It’s a fetching frock with spaghetti straps, an engineered paisley print, and an asymmetrical hemline. And it’s at the center of a law enforcement action against department store chain Lord & Taylor for its allegedly deceptive use of native advertising – the first case of its kind since the FTC released its Enforcement Policy Statement in December. The lawsuit also challenges Lord & Taylor’s “product bomb” campaign on Instagram as misleading. Lord & Taylor used an extensive social media push to launch Design Lab, its own apparel line aimed at women between 18 and 35. The strategy was interesting: Focus on just one item – that paisley asymmetrical dress. For the native advertising part of the campaign, Lord & Taylor signed a contract to have Nylon, an online fashion magazine, run an article about the Design Lab collection featuring a photo of the paisley dress. Lord & Taylor reviewed and approved the paid-for Nylon article, but didn’t require a disclosure about their commercial arrangement. In addition, Lord & Taylor contracted to have Nylon post a photo of the paisley dress on Nylon’s Instagram page. Again, Lord & Taylor reviewed and approved the paid-for post, but didn’t require a disclosure. That was only part of the campaign. Lord & Taylor also recruited a team of fashion influencers, all of whom had two things in common: a sense of style and a massive number of followers on social media platforms. Lord & Taylor gave the dress to 50 influencers and paid them between $1,000 and $4,000 to post photos of themselves in the dress on Instagram on one specified “product bomb” weekend in March 2015 – the same weekend when Nylon posted its Lord & Taylor-approved photo. Style the dress any way you like, Lord & Taylor told the influencers, but in other aspects, the contract was all business. The influencers had to: 1) use the @lordandtaylor Instagram user designation and the campaign hashtag #DesignLab in the photo caption; and 2) tag the photo @lordandtaylor. Lord & Taylor’s reps preapproved each of the influencers’ Instagram posts to make sure they included the required hashtag and Instagram designation. The company also edited some of what the influencers planned to say. But despite the company’s punctilious approach to hashtags, handles, and the like, Lord & Taylor was curiously silent about other key aspects of the campaign. For example, according to the FTC, Lord & Taylor’s contract didn’t require the influencers to disclose that Lord & Taylor had paid them. Furthermore, none of the Instagram posts Lord & Taylor approved included a disclosure that the influencer had received the dress for free, that she had been compensated for the post, or that the post was a part of a Lord & Taylor ad campaign. And as the complaint alleges, Lord & Taylor didn’t add a disclosure to that effect to any of the influencers’ posts it reviewed. The Instagram campaign reached 11.4 million individual users, resulting in 328,000 brand engagements – likes, comments, reposts, etc. – with Lord & Taylor’s Instagram handle. And the paisley dress sold out. The FTC complaint charges Lord & Taylor with three separate violations: 1) that Lord & Taylor falsely represented that the 50 Instagram images and captions reflected the independent statements of impartial fashion influencers, when they really were part of a Lord & Taylor ad campaign to promote sales of its new line; 2) that Lord & Taylor failed to disclose that the influencers were the company’s paid endorsers – a connection that would have been material to consumers; and 3) that Lord & Taylor falsely represented that the Nylon article and Instagram post reflected Nylon’s independent opinion about the Design Lab line, when they were really paid ads. Under the terms of the proposed settlement, Lord & Taylor can’t falsely claim – expressly or by implication – that an endorser is an independent user or ordinary consumer. If there is a material connection between the company and an endorser, Lord & Taylor must clearly disclose it “in close proximity” to the claim. And Lord & Taylor can’t suggest or imply that a paid ad is a statement or opinion from an independent or objective publisher or source. You can file an online comment about the proposed settlement by the April 14, 2016. What does the Lord & Taylor case suggest for your company’s social media campaigns? If you use native advertising, consider the context. As the FTC explained in Native Advertising: A Guide for Businesses, “The watchword is transparency. An advertisement or promotional message shouldn’t suggest or imply to consumers that it’s anything other than an ad.” Review your native ads from the perspective of consumers who don’t have your industry expertise about new forms of promotion. If there is a material connection between your company and an endorser, disclose it. What’s a material connection? According to the FTC’s Endorsement Guides, it’s a connection between the endorser and the seller that might materially affect the weight or credibility a consumer gives the endorsement. Read The FTC’s Endorsement Guides: What People Are Asking for nuts-and-bolts compliance advice and apply those principles if you enlist influencers, bloggers, or others in your marketing efforts. Disclosures of material connection must be clear and conspicuous. What about explaining a material connection in a footnote, behind an obscure hyperlink, or in a general ABOUT ME or INFORMATION page? No, no, and no. As with any disclosure of material information, businesses should put the disclosure in a location where consumers will see it and read it. The terms of the Lord & Taylor settlement apply just to that company, of course, but for prudent marketers, a good rule of thumb is the standard in that order: “in close proximity” to the claim. Train your affiliates and monitor what they’re doing on your behalf. If your company uses social media campaigns like this, make your expectations clear at the outset with influencers and follow through with an effective compliance program. There’s no one-size-fits-all approach, but The FTC’s Endorsement Guides: What People Are Asking lists elements every program should include: Because advertisers are responsible for substantiating objective product claims, explain to your network the claims you can support; Instruct them about their responsibilities for disclosing their connection to you; Periodically search to make sure they’re following your instructions; and Follow up if you spot questionable practices.
- When BOGO is a no-goby lfair on March 6, 2015 at 3:42 pm
When BOGO is a no-go lfair March 6, 2015 | 10:42AM When BOGO is a no-go By Lesley Fair If you watch as much TV as we do, you may have been tempted to reach for the phone to order the Snuggie, that blanket with sleeves for couch potatoes; Forever Comfy, the answer to rump-sprung chairs; or a host of other items sold by New York-based Allstar Marketing Group. And if one Magic Mesh, Cat’s Meow, Roto Punch, or Perfect Tortilla wasn’t enough, the ads reeled buyers in with a “double the offer” buy-one-get-one-free promotion the FTC and New York Attorney General said was misleading. Settlements totaling $8 million offer guidance on how to make sure your BOGO doesn’t turn into a no-go. According to the FTC’s complaint, Allstar deceived consumers about key parts of the transaction. As a result, many people ended up with merchandise they didn’t order and charges they didn’t authorize. For example, Magic Mesh – a self-closing screen for doors – was advertised for “just $19.95.” But “call now” and the company promised to “double the offer. Just pay separate processing and handling fees.” That’s right, said the pitchman, “you get two Magic Mesh curtains for $19.95. That’s less than $10 each.” Now for what the defendant didn’t tell people. First, Allstar charged $7.95 processing and handling for each Magic Mesh. What’s more, it was impossible to decline the BOGO, meaning that the minimum processing and handling fee was $15.90. That bumped the advertised $19.95 offer up to $35.85, without clear upfront disclosures about what consumers would get and how much they’d be billed. The FTC says Allstar’s labyrinth-like telephone and online ordering processes compounded the problem. For example, the toll-free number used an Interactive Voice Recognition system – one of those “Press 1” set-ups that doesn’t offer people the option to speak to an operator. Consumers immediately had to give their credit or debit card numbers and the system didn’t prompt them to indicate how many of an item they wanted. A recorded voice just said, for example, “Great. We have you down for one Magic Mesh set” without clearly explaining that people had to get two screens and pay separate processing and handling for each of them. But wait, there’s more. Allstar then pitched a series of upsells for its own products and for items sold by others. Where it got even more confusing is that Allstar offered consumers “additional sets” of Magic Mesh and asked for the first time how many items people wanted. Because of how the company described the deal, some consumers pressed 1, intending to get just the originally advertised BOGO offer. What they ended up with, however, was four screens – two “sets” – at a hefty additional cost. At no time did Allstar tell people how many products they ordered or the total cost. According to the FTC, Allstar even charged some consumers who hung up mid-call and didn’t intend to complete a sale. You’ll want to read the complaint for the details, but the FTC says Allstar’s online ordering process was no clearer. Faced with multiples of products they didn’t want and charges they didn’t authorize, some consumers turned to Allstar’s “30 day money-back guarantee (less p&h).” The first deterrent was that the processing and handling fees often were close to 50% of the total cost. If consumers called to complain about receiving merchandise they didn’t order, many were refused full refunds and were told they had to return the items at their own expense. The FTC’s complaint alleges that Allstar illegally billed consumers without their express consent and failed to adequately disclose material terms of the offer. The lawsuit also charges the company with multiple violations of the Telemarketing Sales Rule’s provisions regarding upsells. What’s the message for marketers? BOGO stick. The FTC says Allstar stuck it to unwary consumers by structuring the deal in a confusing fashion. It’s unwise to hide the true nature of the transaction behind deceptive “free” claims. “Out of order? You’re out of order!” Savvy marketers know that an out-of-order ordering process can result in frustrated customers and possible violations of the FTC Act. If you choose to use an automated system, take particular care to make sure your prompts and options are easy for consumers to understand. Keep your upsells on the up-and-up. Offering upsells via telemarketing ups your compliance ante. Complying with the Telemarketing Sales Rule offers advice on what the TSR requires. State of the union. Like other recent settlements, this case demonstrates that the FTC and state law enforcers are united in the fight against deception.
- Game over: FTC challenges Sony’s claims for PlayStation Vita and tweets by Deutsch LAby wfg-adm109 on November 25, 2014 at 5:06 pm
Game over: FTC challenges Sony’s claims for PlayStation Vita and tweets by Deutsch LA wfg-adm109 November 25, 2014 | 12:06PM Game over: FTC challenges Sony’s claims for PlayStation Vita and tweets by Deutsch LA By Lesley Fair According to the ads, “It’s a problem as old as gaming itself. Stay home and just keep playing, or get to work on time so your coffee breath boss doesn’t ride you like a rented scooter.” For gamers who face that dilemma, Sony Computer Entertainment America marketed its PlayStation Vita as the solution. But according to a settlement announced by the FTC, Sony didn’t deliver on its promises. The lawsuit also charged that Sony’s ad agency, Deutsch LA, had employees post rave tweets about the PS Vita without disclosing their connection to Deutsch or Sony. Even for gamers who wear out the upholstery in front of the PlayStation, every now and then, they really do need to get off the couch. But how can they keep playing since they can’t take the console with them? Enter the PS Vita. According to the ads, “With Cross Platform Gaming, you can play your PS3 game, pause it, then pick up right where you left off on your Vita.” What’s more, Sony’s ads led people to believe that buying the 3G version – which cost an extra $50 plus monthly fees – would let them engage in live, multiplayer gaming. So what’s the straight story? The FTC says Sony exaggerated the Vita’s capabilities. In fact, users can’t easily access their PS3 games on the PS Vita. Most PS3 games can’t be played remotely because Sony didn’t specifically design the remote play feature into the PS3 system. For example, the popular PS3 game Killzone 3 was featured in a Sony video about remote play, but was never playable remotely on the Vita – and very few, if any, games of a similar size and complexity worked with the remote play feature. What about pausing on the console and picking the game up where you left off with the PS Vita? Good luck with that because according to the complaint, the heavily hyped cross platform feature was available for only a few PS3 games. Here’s an example of how things actually worked – or didn’t work – for many users. Ads for “MLB12: The Show” promised gamers “NEVER STOP PLAYING” and touted “Cross Platform Game Save” that let users “Play on your PS3 system and then continue your game on the go with PS Vita.” But users could pause the game on their console and pick it up on their Vita only after they’d played the entire game – all 9 innings. In addition, Sony didn’t tell gamers that to use this feature, in most cases they had to buy two versions of the same game – one for their PS3 and another for their Vita. What about Sony’s claim that users could engage in live, multiplayer gaming through 3G? Actual game play delivered less than the company promised. According to the complaint, PS Vita users are restricted to “asynchronous” multiplayer gaming – a fancy word for “My turn, then your turn” – and can’t engage in games that feature live, simultaneous play. The complaint challenges Sony’s ad claims as false or misleading. To settle the lawsuit, the company has agreed to offer buyers $25 in cash or a voucher for $50 worth of merchandise from a group of Sony products and services. The FTC’s action against California-based Deutsch LA charges that the ad agency knew or should have known that certain cross platform and live, multiplayer gaming claims for the PS Vita were false. But the allegation of interest to most businesses focuses on the ad agency’s deceptive use of social media to promote the Sony product. According to the complaint, about a month before the Vita debuted, one of Deutsch’s assistant account executives sent this email to all Deutsch employees: Fellow Deutschers – The PlayStation Team has been working hard on a campaign to launch Sony’s all-new handheld gaming device, the PS Vita, and we want YOU to help us kick things off! The PS Vita’s innovative features like 3G gaming, cross platform play and augmented reality will revolutionize the way people game. To generate buzz around the launch of the device, the PS Vita ad campaign will incorporate a #GAMECHANGER hashtag into nearly all creative executions. #GAMECHANGER will drive gamers to Twitter where they can learn more about the PS Vita and join in the conversation. The campaign starts on February 13th, and to get the conversation started, we’re asking YOU to Tweet about the PlayStation Vita using the #GAMECHANGER hashtag. Easy, right? . . . In response, Deutsch employees used their personal Twitter accounts to hype the PS Vita through tweets like: “One thing can be said about PlayStation Vita . . . it’s a #gamechanger” “PS Vita [ruling] the world. Learn about it! us.playstation.com/psvita/#GAMECHANGER” “Thumbs UP #GAMECHANGER – check out the new PlayStation Vita” “This is sick . . . See the new PS Vita in action. The gaming #GameChanger” “Got the chance to get my hands on a PS Vita and I’m amazed how great the graphics are. It’s definitely a #gamechanger!” The complaint alleges that Deutsch’s failure to disclose that tweets were from employees of Sony’s ad agency was deceptive. Interested in weighing in on the proposed settlements? File your comments about Sony or Deutsch by December 29, 2014. If you have clients (or gamers) with questions about the program to get cash back, the proposed order requires Sony to email eligible consumers. Next: Takeaway tips from the cases
- FTC’s Jamster case: 5 tips for mobile marketersby wfg-adm109 on August 22, 2013 at 2:24 pm
FTC’s Jamster case: 5 tips for mobile marketers wfg-adm109 August 22, 2013 | 10:24AM FTC’s Jamster case: 5 tips for mobile marketers By Lesley Fair So people were taking a few minutes to play the free version of Angry Birds on their Android device. At some point between the Giant Slingshot and the Mighty Eagle, they got a “Virus Detected” warning. But according to an FTC lawsuit, that scary-looking security alert was phony and just a way for Jamster (the court papers use the corporate name Jesta Digital) to place charges on people’s cell phone bills without their express consent. Of course, a settlement is legally binding only on that defendant. But if you’re monitoring the mobile market (or making money from it), here are five tips to take from the FTC’s case against Jamster: 1. Long-standing truth-in-advertising principles apply to mobile marketing. “It’s mobile. Anything goes!” How many times have you heard that? We can respond in three words: Wrong, wrong, and wrong. Whether you’re selling Model Ts, poodle skirts, or the latest mobile service, false statements — like Jamster’s phony malware warnings — are illegal under the FTC Act. So enough already with the “anything goes” talk. Like every other advertiser, mobile marketers are covered by federal truth-in-advertising standards. 2. Watch out for WAPacious billing practices. According to the complaint, Jamster used WAP billing, a new-ish method that captures consumers’ mobile phone information and uses it for billing. But often all it takes to trigger WAP billing is a simple tap of a finger on a screen. So consumers may be billed as the result of just pushing a button or two. If companies uses deceptive tactics to get people to push those buttons, a double opt-in won’t immunize them from law enforcement action. 3. Disclose the details clearly and prominently. Many consumers that Jamster illegally billed did nothing more than click a button that said PROTECT YOUR ANDROID TODAY. Buried in fine print was the clear-as-mud statement, “For $9.99/month get 20 credits to use on ringtones and more.” We’ve said it so many times that we really should set up a keyboard shortcut, but here we go again: It’s the law — and it’s always been the law — that if the disclosure of information is necessary to prevent deception, the disclosure must be clear and prominent. Tiny print, buried text, and “It’s all Greek to me” wording won’t work in any medium and most certainly won’t work on the small screen of a mobile device. Parts V and VI of the proposed order offer details on what Jamster has to disclose in the future and how they have to disclose it. Another resource for companies looking for guidance: .com Disclosures: How to Make Effective Disclosures in Digital Advertising. 4. Mobile missteps can be costly. The order requires Jamster to automatically provide full refunds to broad categories of consumers who were illegally billed. What’s more, Jamster has to send texts to other affected consumers with information on how to apply for a refund, and has to work with AT&T and T-Mobile to place notices in people’s mobile bills. On top of that, Jamster will pay $1.2 million to settle the lawsuit. Add it up and it totals trouble for companies that bill people illegally. 5. Cut out cramming. The mobile marketplace is booming, but future success depends on transparency and trustworthiness. Through reports, national roundtables and workshops, and ongoing law enforcement, the FTC’s message couldn’t be clearer: It’s time to drop the hammer on mobile cramming.
- Watch what you’re doing with time-barred debtsby wfg-adm109 on January 30, 2012 at 3:56 pm
Watch what you’re doing with time-barred debts wfg-adm109 January 30, 2012 | 10:56AM Watch what you’re doing with time-barred debts By Lesley Fair Of course, people are responsible for their debts. However, at a certain point, how much time has passed becomes an affirmative defense under state law and creditors can’t prevail in court. But what happens if a payment is made on a time-barred debt? A consumer can really get clocked — because in many states the debt can be revived if a person makes a payment or says in writing that they intend to. The FTC has announced a $2.5 million settlement with Asset Acceptance, LLC, for allegedly breaking the law in how it tried to collect time-barred debts. Michigan-based Asset Acceptance buys unpaid debts from credit card companies, health clubs, companies that provide telecom or utility service, and other debt buyers. Getting the debts for pennies on the dollar, the company targets accounts other collectors have pursued unsuccessfully and are more than a year past due. The problem, of course, is that if a debt collector tells somebody they owe money and demands payment, it may create the misleading impression that the company can collect in court. That’s not the case with time-barred debts. A law enforcement action filed by the Department of Justice on the FTC’s behalf charges that Asset Acceptance pursued debts — including time-barred debts — in ways that violated the law. Among other things, the complaint alleges that the company: claimed that consumers owed money when Asset Acceptance didn’t have proof to back it up; failed to disclose that debts were too old to be legally enforceable or that a partial payment would restart the clock; failed to give consumers verification of a debt when they asked for it; provided information to credit reporting agencies it knew — or had reasonable cause to know — was inaccurate; didn’t notify consumers in writing that it passed negative information on to credit reporting agencies; didn’t conduct reasonable investigations when it got a notice of dispute from a credit reporting agency; illegally told third parties about people’s debts; and used illegal debt collection practices. In addition to the $2.5 million civil penalty, the settlement puts provisions in place to protect consumers going forward. For example, when dealing with debt it knows or should know is time-barred, Asset Acceptance must disclose to the consumer that it won’t sue on the debt and — assuming it’s the case — it has to tell people that it may report nonpayment to the credit bureaus. Once it has made that disclosure, Asset Acceptance can’t sue, even if the consumer makes a partial payment that otherwise would restart the limitations clock. The order also prohibits Asset Acceptance from making material misrepresentations about debts; from “parking” debt on a consumer’s credit report when it has failed to notify them in writing; and from violating the FTC Act, the Fair Credit Reporting Act, and the Fair Debt Collection Practices Act in the ways alleged in the complaint.
- Free means free, says the FTCby wfg-adm109 on May 23, 2011 at 7:37 pm
Free means free, says the FTC wfg-adm109 May 23, 2011 | 3:37PM Free means free, says the FTC By Lesley Fair You can swim freestyle. You can work freelance. And there are those among us who still hold up lighters and yell “Play Free Bird.” But for marketers, one thing you can’t do is advertise a product as free and then bill customers’ credit cards — not once and certainly not over and over and over again. The legal theories advanced in the pending case against Canadian Jesse Willms, ten companies the FTC says he controls, and other individual and corporate defendants aren’t new. What’s noteworthy is the sheer scope of the international enterprise: The FTC says the defendants raked in more than $467 million from consumers in the US, Canada, UK, Australia and New Zealand through an elaborate scheme of false product claims, unauthorized celebrity endorsements, forced upsells, undisclosed terms and conditions, unauthorized charges, and ruses designed to evade the credit card industry’s risk management system. The FTC’s complaint is a veritable travelog of deceptive practices allegedly perpetrated by individuals using a labyrinth of corporations registered in Edmonton, Alberta; Surrey, England; Idaho Falls, Idaho; Nicosia, Cyprus; and points between. The lawsuit alleges the defendants used a vast global network of online affiliate marketers to peddle everything from acai berry diet miracles, teeth whiteners, and anti-colon cancer products to work-at-home schemes, government grant programs, free credit reports, and penny auctions. The ads were ubiquitous and often featured eye-catching — and unauthorized — “endorsements” from Oprah Winfrey and Rachael Ray. In addition, the complaint charges that the defendants plastered their websites with the logos of “60 Minutes,” CNN, MSNBC, USA Today, CBS, and other media outlets, despite the fact that none of them had endorsed or positively reported on any of the products. One hallmark of the scheme, says the FTC, were promises of “free trials” that opened an illegal pipeline to consumers’ credit card and bank accounts. Once the defendants had the account info, the FTC claims they really went to town, posting monthly charges on people’s accounts without their authorization and after expressly representing the transaction as “free.” According to the complaint, when the defendants “disclosed” the details, they used every trick in the Fineprint Playbook: tiny type, pale colors, dense blocks of text, hard-to-find terms and conditions, streaming video to draw customers’ attention away from information critical to their purchase decision, etc. The complaint also challenges the defendants’ refund policies as deceptive. The defendants typically advertised that their products came with an “Iron-clad 60-day Moneyback Guarantee” or a “100% satisfaction guarantee,” and that buyers could easily get “no questions asked” full refunds. But according to the FTC, the defendants failed to clearly disclose the numerous hoops consumers had to jump through to get their money back or to stop the incessant automatic shipment of unwanted merchandise. In many cases, buyers had to return the product at their own expense before the end of the “trial” period — which, in the case of digital products like work-at-home programs, was as short as 24 hours. Some buyers received refunds only after complaining to law enforcers or the Better Business Bureau. Even then, the defendants often gave just a portion of their money back. One interesting note for FTC pleadings watchers. It’s no surprise the defendants’ business practices generated a high rate of chargebacks — sometimes 10 to 20 times higher than the ratio allowed by credit card companies — which caused merchant banks to terminate them and place them on what industry insiders call the MATCH list. According to the FTC, rather than clean up their act, the defendants engaged in an elaborate scheme to create new shell corporations ostensibly headed by other people, although the defendants remained in the driver’s seat. They applied for merchant accounts using the shell corporations that couldn’t easily be traced back to them. That way, they were able to continue to process unauthorized charges, leading to widespread consumer injury. In addition, when merchant banks and others involved in payment processing told them their websites didn’t adequately disclose the terms of the offer, the complaint alleges the defendants created clean “dummy” sites to fool them into thinking they’d changed their practices. The lawsuit alleges that the defendants’ evasion of credit card risk management systems was an unfair practice, in violation of Section 5. In addition, the FTC’s complaint alleges violations of the Electronic Fund Transfer Act and Reg E. The lawsuit also charges that the defendants’ weight loss and cancer prevention representations for AcaiBurn and PureCleanse were false and unsubstantiated, including their claim that the products were backed by placebo-controlled clinical studies. The case is pending in federal court in Seattle.

FTC Business Blog
We are an ethical website cyber security team and we perform security assessments to protect our clients.