Compass Security Offensive Defense
Compass Security Blog Offensive Defense
- From Folder Deletion to Admin: Lenovo Vantage (CVE‑2025‑13154)by John Ostrowski on February 10, 2026 at 8:00 am
Last year we wrote about a Windows 11 vulnerability that allowed a regular user to gain administrative privileges. Not long after, Manuel Kiesel from Cyllective AG reached out to us after stumbling across a seemingly similar issue while investigating the Lenovo Vantage application. It turns out that the exploit primitive for arbitrary file deletion to gain SYSTEM privileges no longer works on current Windows machines.
- Continuous Learning – Inside our Internal Security Trainingby Sylvain Heiniger on January 20, 2026 at 9:00 am
Over the course of 2025, we performed several hundred security assessments for our clients. In each of these, security analysts must understand a new environment and often work with unfamiliar technologies. Even for well-known technologies, things change rapidly. Quick learning and adaptability are essential skills. To keep our security analysts sharp and up to date, we regularly attend security conferences, external courses and trainings but also organize internal sessions. It has become a tradition for us to spend the first week of January learning new things, starting the year improving our know-how.
- NTLM Relaying to HTTPSby Sylvain Heiniger on November 26, 2025 at 8:00 am
NTLM is the legacy authentication protocol in Windows environment. In the past few years, I’ve had the opportunity to write on this blog about NTLM Relaying to DCOM (twice), to AD CS (ESC11) and to MSSQL. Today I will look back on relaying to HTTPS and how the tooling improved.
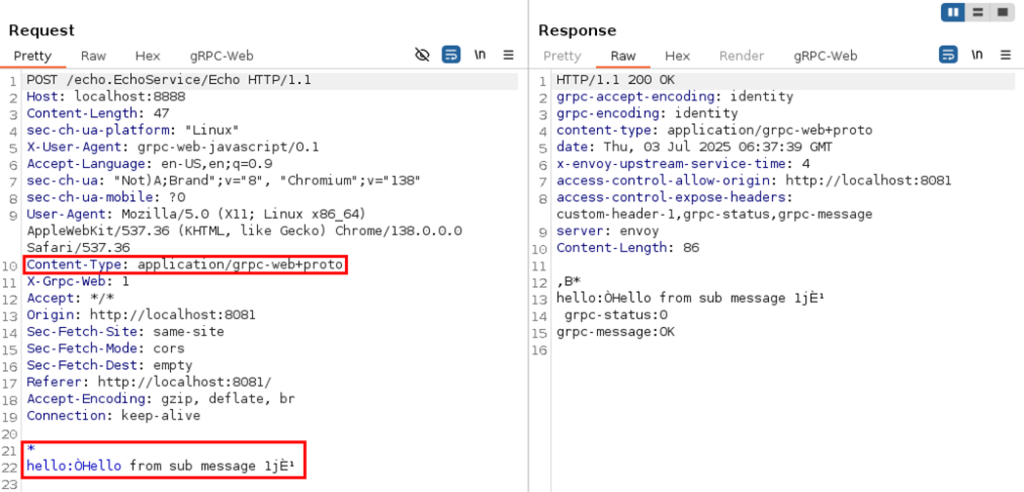
- bRPC-Web: A Burp Suite Extension for gRPC-Webby Urs Müller on October 21, 2025 at 7:00 am
The gRPC framework, and by extension gRPC-Web, is based on a binary data serialization format. This poses a challenge for penetration testers when intercepting browser to server communication with tools such as Burp Suite. This project was initially started after we unexpectedly encountered gRPC-Web during a penetration test a few years ago. It is important to have adequate tooling available when this technology appears. Today, we are releasing our Burp Suite extension bRPC-Web in the hope that it will prove useful to others during their assessments.
- LockBit Breach: Insights From a Ransomware Group’s Internal Databy Andreas Arnold on October 7, 2025 at 7:00 am
Something a bit wild happened recently: A rival of LockBit decided to hack LockBit. Or, to put this into ransomware-parlance: LockBit got a post-paid pentest. It is unclear if a ransomware negotiation took place between the two, but if it has, it was not successful. The data was leaked. Now, let’s be honest: the dataset is way too small to make any solid statistical claims. Having said that, let’s make some statistical claims!
- Ensuring NIS2 Compliance: The Importance of Penetration Testingby Stephan Sekula on September 23, 2025 at 7:00 am
The Network and Information Security Directive 2 (NIS2) is the European Union’s latest framework for strengthening cyber security resilience across critical sectors. If your organization falls within the scope of NIS2, understanding its requirements and ensuring compliance is crucial to avoiding penalties and securing your operations against cyber threats.
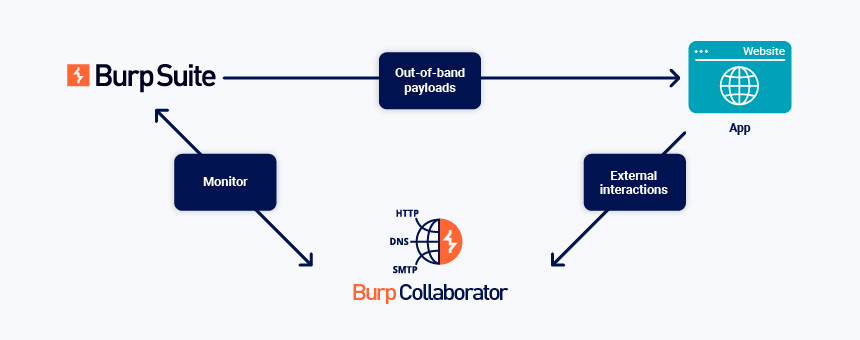
- Collaborator Everywhere v2by Andreas Brombach on September 9, 2025 at 7:00 am
Collaborator Everywhere is a well-known extension for Burp Suite Professional to probe and detect out-of-band pingbacks. We developed an upgrade to the existing extension with several new exiting features. Payloads can now be edited, interactions are displayed in a separate tab and stored with the project file. This makes it easier to detect and analyze any out-of-band communication that typically occurs with SSRF or Host header vulnerabilities.
- Taming The Three-Headed Dog -Kerberos Deep Dive Seriesby Alex Joss on September 2, 2025 at 7:00 am
Kerberos is the default authentication protocol in on-prem Windows environments. We’re launching a 6-part YouTube series, a technical deep dive into Kerberos. We’ll break down the protocol, dissect well-known attacks, and cover defensive strategies to keep your environment secure.
- Into the World of Passkeys: Practical Thoughts and Real-Life Use Casesby Cyrill Brunschwiler on August 26, 2025 at 7:00 am
In a previous blog post, we explored the technical side of passkeys (also known as discoverable credentials or resident keys), what they are, how they work, and why they’re a strong alternative to passwords. Today, we’ll show how passkeys are used in the real world – by everyday users and security professionals alike.
- xvulnhuntrby Nicolo Fornari on July 8, 2025 at 7:00 am
In 2024 we looked at the possibility of leveraging open weights LLMs for source code analysis. The answer was clearly negative, as a small code base could easily take 200K tokens, more than any context window offered by open weights models. The table below summarizes the top LLMs by context window as of today. Context