- Hacking the grid: How digital sabotage turns infrastructure into a weaponby Saman Zonouz, Associate Professor of Cybersecurity and Privacy and Electrical and Computer Engineering, Georgia Institute of Technology on January 22, 2026 at 1:34 pm
The US used a cyberattack to turn off power in Caracas during the raid to seize Maduro. The US grid is also vulnerable to this kind of attack.
- NZ’s health data hack needs a proper diagnosis – and a transparent treatment planby Dylan A Mordaunt, Research Fellow, Faculty of Education, Health, and Psychological Sciences, Te Herenga Waka — Victoria University of Wellington; Flinders University; The University of Melbourne on January 13, 2026 at 5:31 pm
After two cyber incidents in as many weeks, attention has focused on how the hacks happened. The harder question is how to prevent a repeat.
- An AI lab says Chinese-backed bots are running cyber espionage attacks. Experts have questionsby Toby Murray, Professor of Cybersecurity, School of Computing and Information Systems, The University of Melbourne on November 17, 2025 at 3:57 am
Anthropic says its Claude Code tool was used in a sophisticated, automated campaign to steal sensitive information.
- OpenAI’s Atlas browser promises ultimate convenience. But the glossy marketing masks safety risksby Uri Gal, Professor in Business Information Systems, University of Sydney on October 28, 2025 at 2:29 am
If you want to try Atlas, the advice is straightforward: extreme caution.
- Federal shutdown deals blow to already hobbled cybersecurity agencyby Richard Forno, Teaching Professor of Computer Science and Electrical Engineering, and Associate Director, UMBC Cybersecurity Institute, University of Maryland, Baltimore County on October 7, 2025 at 6:14 pm
The triple whammy of deep staff cuts, shutdown furloughs and the expiration of an information-sharing law leaves national cybersecurity in a perilous state.
- As long as the cybercriminals’ business model works, companies are vulnerable to attackby Ayman El Hajjar, Senior Lecturer & Head of the Cyber Security Research Group, University of Westminster on October 7, 2025 at 3:46 pm
Cybercrime is now a service that crooks can pay for to target businesses for extortion.
- What are ShinyHunters, the hackers that attacked Google? Should we all be worried?by Jennifer Medbury, Lecturer in Intelligence and Security, Edith Cowan University on September 2, 2025 at 11:58 pm
With cyber crime groups constantly shifting tactics and getting creative, we all must stay vigilant – especially if we work at large companies.
- How can we stay safe after data breaches? Step 1 is to change the cybersecurity lawsby Adam Andreotta, Lecturer, School of Management and Marketing, Curtin University on July 10, 2025 at 2:20 am
Ritual apologies after data breaches only go so far. We need better laws to stop these incidents happening at all.
- Cyber crime and real-world crime are converging in a dangerous new way – here’s how to stay safeby Jongkil Jay Jeong, Senior Fellow, School of Computing and Information System, The University of Melbourne on July 10, 2025 at 12:56 am
What happens next when your data is leaked in a data breach like the one at Qantas? Cyber criminals have creative ways to get what they want.
- Selling your old laptop or phone? You might be handing over your data tooby Ritesh Chugh, Associate Professor, Information and Communications Technology, CQUniversity Australia on April 7, 2025 at 8:09 pm
But there are some simple steps you can take to keep your personal information safe.
- Trump has fired a major cyber security investigations body. It’s a risky moveby Toby Murray, Professor of Cybersecurity, School of Computing and Information Systems, The University of Melbourne on January 23, 2025 at 11:45 pm
The well-respected Cyber Safety Review Board investigated some of the worst cyber security attacks in US history. Now, it faces an uncertain future.
- Selling fear: Marketing for cybersecurity products often leaves consumers less secureby Doug Jacobson, Professor of Electrical and Computer Engineering, Iowa State University on January 2, 2025 at 1:27 pm
Ever feel like throwing up your hands and giving up on taking control of your online security? How technology companies market their cybersecurity products might have something to do with that.
- As an ethical hacker, I can’t believe the risks people routinely take when they access the internet in publicby Christopher Patrick Hawkins, Lecturer in Cyber Security and Computer Science, University of Staffordshire on October 8, 2024 at 4:25 pm
If you’re tempted to do a make a couple of cheeky payments while waiting for the band to come on, think again.
- Exploding pagers and walkie-talkies are a reminder of how easily your devices can be hacked – here’s how to make sure they are safeby Nick Hajli, AI Strategist and Professor of Digital Strategy, Loughborough University on September 24, 2024 at 4:04 pm
There are many ways of breaking into your devices. Make sure you safeguard against them.
- How cyberattacks on offshore wind farms could create huge problemsby Kimberly Tam, Associate Professor in Cyber Security, University of Plymouth on September 5, 2024 at 4:15 pm
AI could help close cybersecurity vulnerabilities at offshore wind farms.
- FraudGPT and other malicious AIs are the new frontier of online threats. What can we do?by Bayu Anggorojati, Assistant Professor, Cyber Security, Monash University on July 24, 2024 at 12:19 am
Widely available AI tools are supercharging cyber crime, which means we need to stay on top of our online security like never before.
- CrowdStrike crash showed us how invasive cyber security software is. Is there a better way?by Toby Murray, Associate Professor of Cybersecurity, School of Computing and Information Systems, The University of Melbourne on July 23, 2024 at 2:28 am
Software like Crowdstrike Falcon can access core computer systems and, essentially, spy on everything. We live with these tradeoffs – but perhaps we don’t have to.
- To guard against cyberattacks in space, researchers ask ‘what if?’by Patrick Lin, Professor of Philosophy, California Polytechnic State University on July 3, 2024 at 12:23 pm
Sabotaged space stations, falsified space probe data and faked alien contact are just a few of the scenarios a report on space cybersecurity outlines.
- We analysed the entire web and found a cybersecurity threat lurking in plain sightby Kevin Saric, Computer Scientist & Mechatronic Engineer, CSIRO on June 28, 2024 at 1:33 am
Think you can trust every website? One typo and you could be caught in a phishing trap.
- Chinese nationalist groups are launching cyber-attacks – often against the wishes of the governmentby Lewis Eves, Teaching Associate in Politics and International Relations, University of Sheffield on May 14, 2024 at 1:42 pm
The Chinese Communist Party has inadvertently given the country’s nationalist movement influence that it’s struggling to contain.
- Cybersecurity researchers spotlight a new ransomware threat – be careful where you upload filesby Selcuk Uluagac, Professor of Computing and Information Science, Florida International University on April 26, 2024 at 12:28 pm
Modern web browsers are increasingly becoming like virtual computers, able to send email and play music and videos. The downside is it’s a new way for hackers to get into your computer.
- AI is making smart devices – watches, speakers, doorbells – easier to hack. Here’s how to stay safeby Chao Chen, Deputy Director, Enterprise AI and Data Analytics Hub, RMIT Univeristy, RMIT University on April 17, 2024 at 5:38 am
With 17 billion internet-connected devices worldwide, AI is subtly creeping into our everyday lives – and making us more vulnerable to cyberattacks.
- What is Volt Typhoon? A cybersecurity expert explains the Chinese hackers targeting US critical infrastructureby Richard Forno, Principal Lecturer in Computer Science and Electrical Engineering, University of Maryland, Baltimore County on March 29, 2024 at 12:46 pm
Chinese state-sponsored hackers are targeting critical infrastructure. Here’s what they’re doing, how the US government is responding and how you can help.
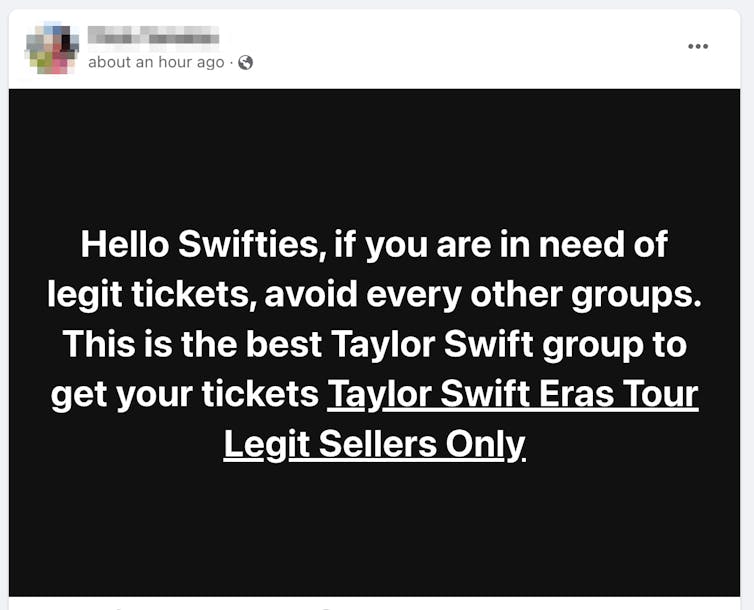
- Desperate for Taylor Swift tickets? Here are cybersecurity tips to stay safe from scamsby Cassandra Cross, Associate Dean (Learning & Teaching) Faculty of Creative Industries, Education and Social Justice, Queensland University of Technology on February 9, 2024 at 12:56 am
Australian fans who didn’t manage to snag Eras tickets are on the hunt – and scammers are capitalising on this. Here’s everything you need to know to protect yourself.
- Cybercrime victims who aren’t proficient in English are undercounted – and poorly protectedby Fawn Ngo, Associate Professor of Criminology, University of South Florida on January 29, 2024 at 1:35 pm
The federal government’s web portal for reporting cybercrimes is of little use if you have limited proficiency with English.

Hackers
We are an ethical website cyber security team and we perform security assessments to protect our clients.