Online Security The Conversation
- The American TikTok deal doesn’t address the platform’s potential for manipulation, only who profitsby Andrew Buzzell, Postdoctoral Fellow, Rotman Institute of Philosophy, Western University on October 2, 2025 at 3:26 pm
U.S. President Donald Trump signed an executive order approving a deal that allows U.S. businesspeople to acquire ownership of TikTok.
- How can you stay safe from cyber attacks? Here are 2 simple checklists from expertsby Jing Jia, Senior Lecturer, Business School, University of Newcastle on December 16, 2024 at 11:15 pm
Cyber attacks can cost you tens of thousands of dollars. Expert advice can help you stay safe – and it’s not complicated.
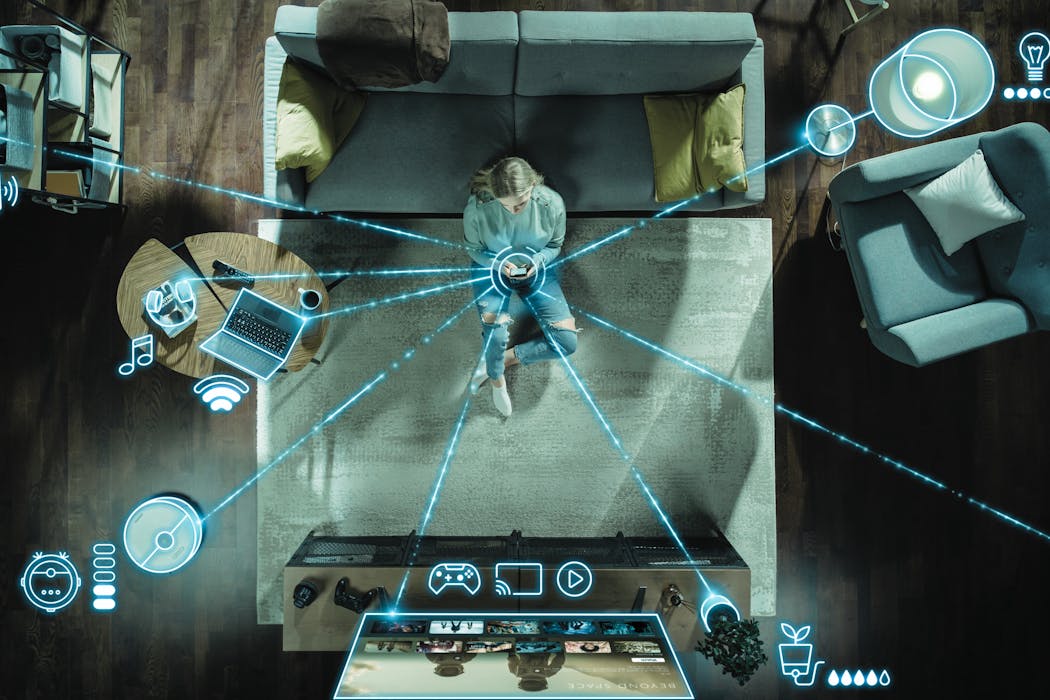
- Speakers, vacuums, doorbells and fridges – the government plans to make your ‘smart things’ more secureby Abu Barkat ullah, Associate Professor of Cyber Security, University of Canberra on October 15, 2024 at 2:52 am
The Australian government wants to introduce ‘minimum security standards’ for all smart devices. What will that look like?
- FraudGPT and other malicious AIs are the new frontier of online threats. What can we do?by Bayu Anggorojati, Assistant Professor, Cyber Security, Monash University on July 24, 2024 at 12:19 am
Widely available AI tools are supercharging cyber crime, which means we need to stay on top of our online security like never before.
- Australia will trial ‘age assurance’ tech to bar children from online porn. What is it and will it work?by Paul Haskell-Dowland, Professor of Cyber Security Practice, Edith Cowan University on May 2, 2024 at 6:24 am
The Australian government will test tools to shield kids from inappropriate material online. Even though there’s no one easy fix, these checks could help.
- Phishing scams: 7 safety tips from a cybersecurity expertby Thembekile Olivia Mayayise, Senior Lecturer, University of the Witwatersrand on December 14, 2023 at 1:40 pm
Cybercriminals don’t take breaks, so you shouldn’t ever drop your guard.
- Should you pay for Meta’s and Twitter’s verified identity subscriptions? A social media researcher explains how the choice you face affects everyone elseby Anjana Susarla, Professor of Information Systems, Michigan State University on March 8, 2023 at 1:40 pm
Twitter and Meta are looking to make money from protecting users’ identities. This raises questions about collective security, people understanding what they’re paying for and who remains vulnerable.
- Apple’s PassKeys update could make traditional passwords obsoleteby Paul Haskell-Dowland, Professor of Cyber Security Practice, Edith Cowan University on September 11, 2022 at 8:10 pm
The advice for years has been to use password managers. But even these don’t completely eliminate the risk of being compromised.
- Is Russia really about to cut itself off from the internet? And what can we expect if it does?by Mohiuddin Ahmed, Lecturer of Computing & Security, Edith Cowan University on March 10, 2022 at 3:43 am
The Kremlin is pushing for a quick migration of all Russian websites and services to be hosted within the country. It could be the first stage of a larger disconnection effort.
- Crypto theft is on the rise. Here’s how the crimes are committed, and how you can protect yourselfby Aaron M. Lane, Senior Lecturer in Law, RMIT University on February 3, 2022 at 5:59 am
Although it’s estimated illicit activity amounts to less than 1% of all cryptocurrency transactions, figures of losses are still staggering – and on the rise.
- Stop blaming people for choosing bad passwords – it’s time websites did more to helpby Steven Furnell, Professor of Cyber Security, University of Nottingham on January 3, 2022 at 10:33 am
It’s time to think differently about how we address the password problem.
- How an app to decrypt criminal messages was born ‘over a few beers’ with the FBIby David Tuffley, Senior Lecturer in Applied Ethics & CyberSecurity, Griffith University on June 8, 2021 at 7:36 am
The AN0M app was programmed by law enforcement to allow ‘back-door’ access. This led to the retrieval of information that culminated in hundreds of search warrants.
- Facebook data breach: what happened and why it’s hard to know if your data was leakedby Paul Haskell-Dowland, Associate Dean (Computing and Security), Edith Cowan University on April 6, 2021 at 5:22 am
More than 500 million people’s details were compromised. The records include various combinations of name, email, gender, date of birth, location, relationship status and employer.
- RMIT attack underlines need to train all uni staff in cyber safetyby Abu Barkat ullah, Associate Professor of Cyber Security, University of Canberra on February 28, 2021 at 7:06 pm
Universities are a prime target for cyber attacks and the weakest links in their defences are all the non-expert users of their systems. Teaching everyone basic cyber hygiene is vital.
- How to encourage cyber-safe behaviour at work without becoming the office grouchby Nathalie Collins, Academic Director (National Programs), Edith Cowan University on February 26, 2021 at 3:16 am
If you’re reluctant to share your password, or broadcast a team password in Slack in a groupchat, your instincts are correct. But mocking those who ‘do the wrong thing’ is unlikely to help.
- The Christmas gifts that keep giving (your data away) — and how to prevent thisby Paul Haskell-Dowland, Associate Dean (Computing and Security), Edith Cowan University on January 4, 2021 at 7:08 pm
Many of us will have received new gadgets this festive season. But how can we ensure these are set up safely? And what’s the best way to discard of old devices being replaced?
- A computer can guess more than 100,000,000,000 passwords per second. Still think yours is secure?by Paul Haskell-Dowland, Associate Dean (Computing and Security), Edith Cowan University on September 15, 2020 at 5:01 am
One website dedicated to tracking stolen passwords suggests there are details of currently more than 10 billion compromised accounts available online.
- Can I still be hacked with 2FA enabled?by David Tuffley, Senior Lecturer in Applied Ethics & CyberSecurity, Griffith University on September 3, 2020 at 8:01 pm
Two-factor authentication is certainly an added layer of security as we traverse the online world. But it comes in various forms, and they’re not all equally protective.
- Videoconferencing keeps people connected while the coronavirus keeps them inside – but privacy and security are far from perfectby Elizabeth Stoycheff, Associate Professor of Communication, Wayne State University on April 10, 2020 at 12:17 pm
Zoom’s privacy and security shortcomings are just the latest videoconferencing vulnerabilities. Knowing each platform’s risks can help people avoid many of the downsides of virtual gatherings.
- Quantum internet: the next global network is already being laidby Harun Šiljak, Postdoctoral Research Fellow in Complex Systems Science for Telecommunications, Trinity College Dublin on February 18, 2020 at 12:55 pm
Quantum communication is needed to make the internet much more secure.
- Australia’s National Digital ID is here, but the government’s not talking about itby Patrick Scolyer-Gray, Research Fellow, Cyber Security, Deakin University on January 27, 2020 at 6:52 pm
A new digital ID system will gather piles of personal information in one place – and you won’t have full control over who has access
- Facebook’s push for end-to-end encryption is good news for user privacy, as well as terrorists and paedophilesby Roberto Musotto, Cyber Security Cooperative Research Centre Postdoctoral Fellow, Edith Cowan University on December 16, 2019 at 5:24 am
Facebook is planning to put end-to-end encryption on all its messaging services soon. But governments aren’t happy about it, as it could make it harder to catch criminals.
- Data lakes: where big businesses dump their excess data, and hackers have a field dayby Mohiuddin Ahmed, Lecturer of Computing & Security, Edith Cowan University on October 22, 2019 at 4:56 am
A major cyber attack on a data lake could have immense consequences for any of us. And the damage could be felt anywhere from banking to the healthcare sector.
- Apple iPhones could have been hacked for years – here’s what to do about itby Leslie Sikos, Lecturer, Edith Cowan University on September 4, 2019 at 7:52 pm
The news that malware can invade iPhones and other Apple devices via the Safari web browser has damaged Apple’s reputation for security. But you can fix the problem by updating your phone’s software.
- Think Facebook can manipulate you? Look out for virtual realityby Elissa M. Redmiles, Ph.D. Student in Computer Science, University of Maryland on March 21, 2018 at 10:43 am
As the internet-connected world reels from revelations about personalized manipulation based on Facebook data, a scholar of virtual reality warns there’s an even bigger crisis of trust on the horizon.