Threat Research | HPE Juniper Networking Blogs Insights and expertise
- Invisible obfuscation technique used in PAC attackby Asher Langton on February 18, 2025 at 6:28 pm
HPE Juniper Networking Blogs Invisible obfuscation technique used in PAC attack While investigating a sophisticated phishing attack targeting affiliates of a major American political action committee (PAC) in early January 2025, Juniper Threat Labs observed a new JavaScript obfuscation technique. This The post Invisible obfuscation technique used in PAC attack appeared first on HPE Juniper Networking Blogs.
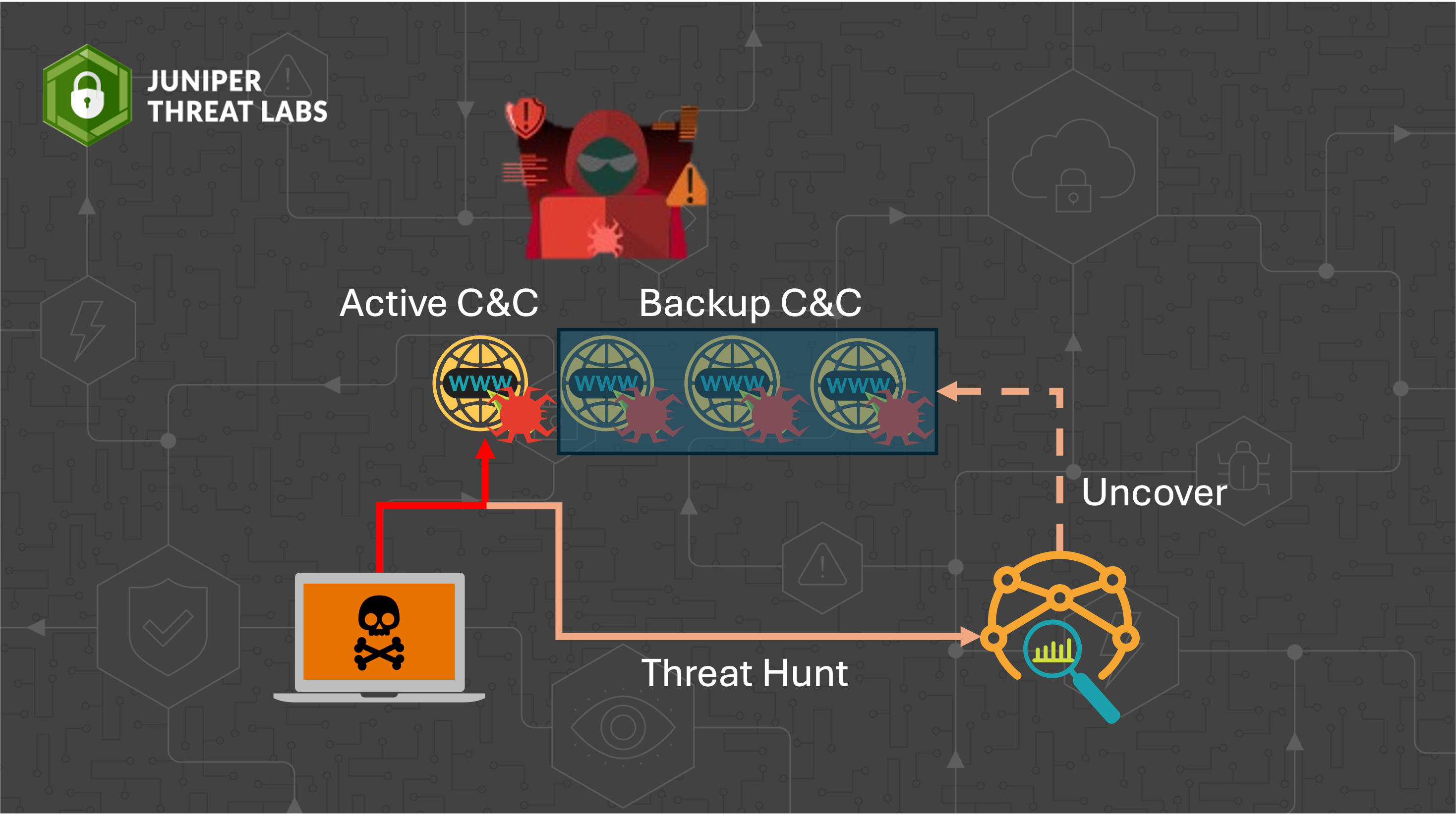
- Threat Hunting with passive DNS: Discovering the Attacker Infrastructureby Omar on December 9, 2024 at 4:00 pm
HPE Juniper Networking Blogs Threat Hunting with passive DNS: Discovering the Attacker Infrastructure Understanding how attackers establish and maintain their attack infrastructure is important for building robust defenses. Attackers employ various tactics to keep their operations resilient and undetected. In this blog post, The post Threat Hunting with passive DNS: Discovering the Attacker Infrastructure appeared first on HPE Juniper Networking Blogs.
- The Hidden Door: How CVE-2024-23897 Enabled Ransomware Attack on Indian Banksby Shwetanjali Rasal on August 13, 2024 at 1:00 pm
HPE Juniper Networking Blogs The Hidden Door: How CVE-2024-23897 Enabled Ransomware Attack on Indian Banks On August 1, 2024, Retail payments began to be disrupted in Indian banks and suddenly, massive news broke, stating Brontoo Technology Solutions – a collaborator with C-Edge Technologies, which is The post The Hidden Door: How CVE-2024-23897 Enabled Ransomware Attack on Indian Banks appeared first on HPE Juniper Networking Blogs.
- BianLian Ransomware Group: 2024 Activity Analysisby Paul Kimayong on July 11, 2024 at 1:00 pm
HPE Juniper Networking Blogs BianLian Ransomware Group: 2024 Activity Analysis Since its emergence in 2022, the BianLian ransomware group has rapidly evolved, showcasing sophisticated techniques and adapting to the shifting landscape of cyber threats. It’s among the top three most The post BianLian Ransomware Group: 2024 Activity Analysis appeared first on HPE Juniper Networking Blogs.
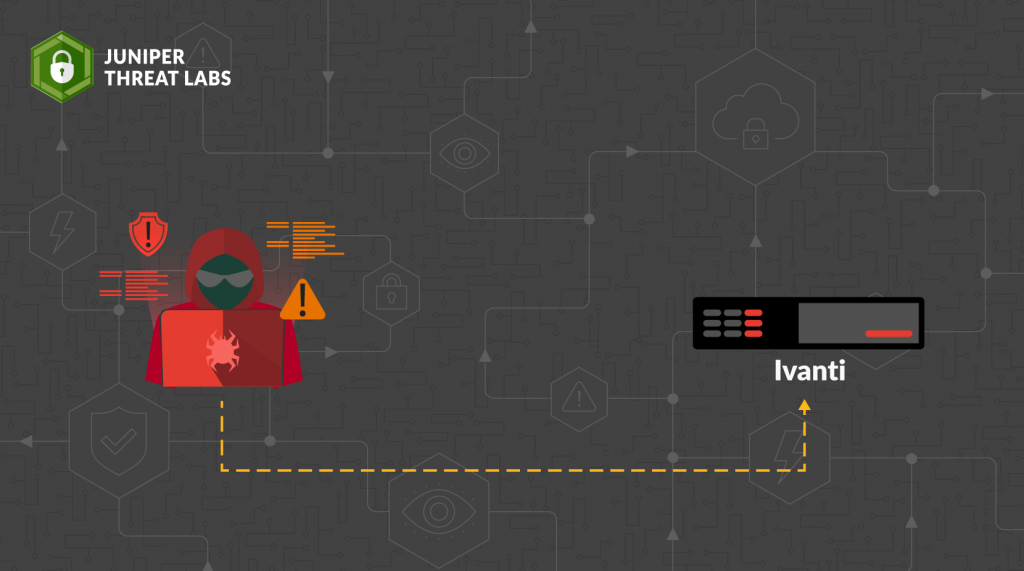
- Protecting Networks from Opportunistic Ivanti Pulse Secure Vulnerability Exploitationby Kashinath T Pattan on May 7, 2024 at 1:30 pm
HPE Juniper Networking Blogs Protecting Networks from Opportunistic Ivanti Pulse Secure Vulnerability Exploitation Juniper Threat Labs has been monitoring exploitation attempts targeting an Ivanti Pulse Secure authentication bypass with remote code execution vulnerabilities. We have observed instances of Mirai botnet delivery in The post Protecting Networks from Opportunistic Ivanti Pulse Secure Vulnerability Exploitation appeared first on HPE Juniper Networking Blogs.
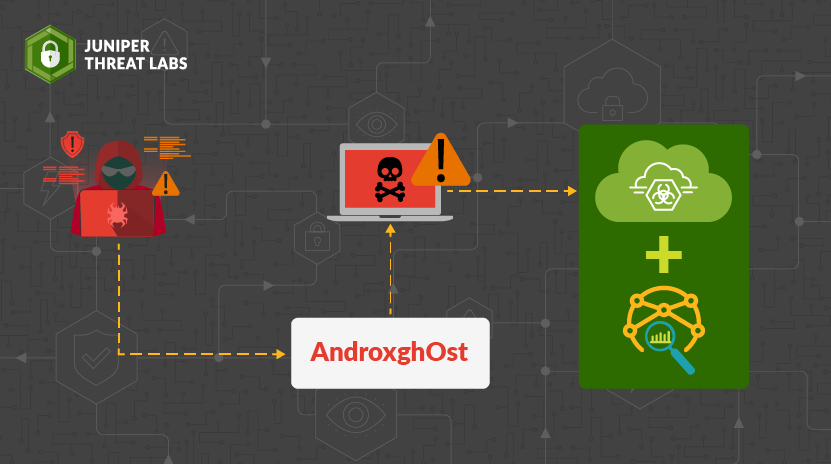
- Shielding Networks From Androxgh0stby Kashinath T Pattan on March 19, 2024 at 9:02 am
HPE Juniper Networking Blogs Shielding Networks From Androxgh0st AndroxGh0st is a Python-based malware designed to target Laravel applications. It works by scanning and taking out important information from .env files, revealing login details linked to AWS and The post Shielding Networks From Androxgh0st appeared first on HPE Juniper Networking Blogs.
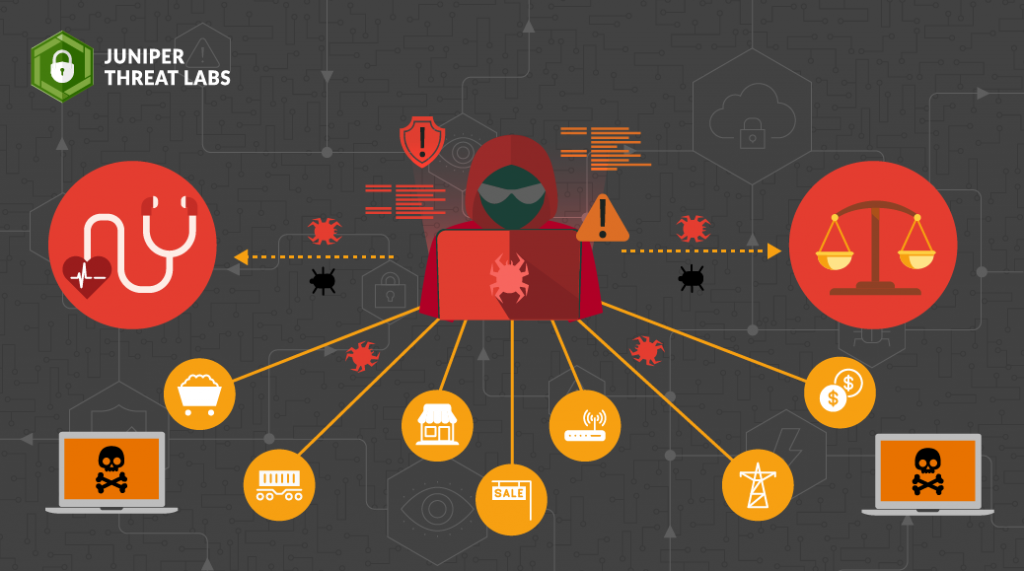
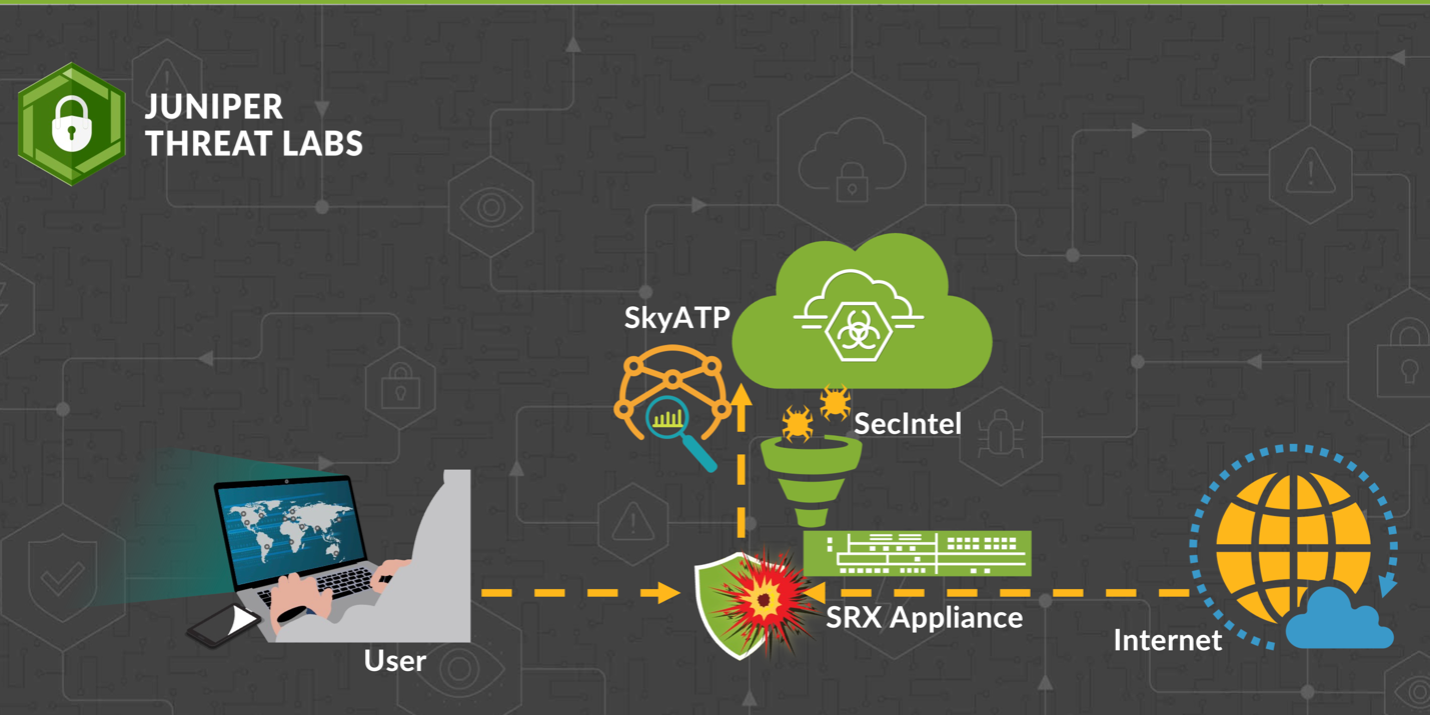
- Real-Time Defense: Analyzing Emerging Cyber Threatsby Omar on February 1, 2024 at 7:30 pm
HPE Juniper Networking Blogs Real-Time Defense: Analyzing Emerging Cyber Threats In this blog, we will dive into the attack trends observed across our customers’ networks. First, we will highlight how the security threat intelligence in the Juniper Advanced Threat Prevention The post Real-Time Defense: Analyzing Emerging Cyber Threats appeared first on HPE Juniper Networking Blogs.
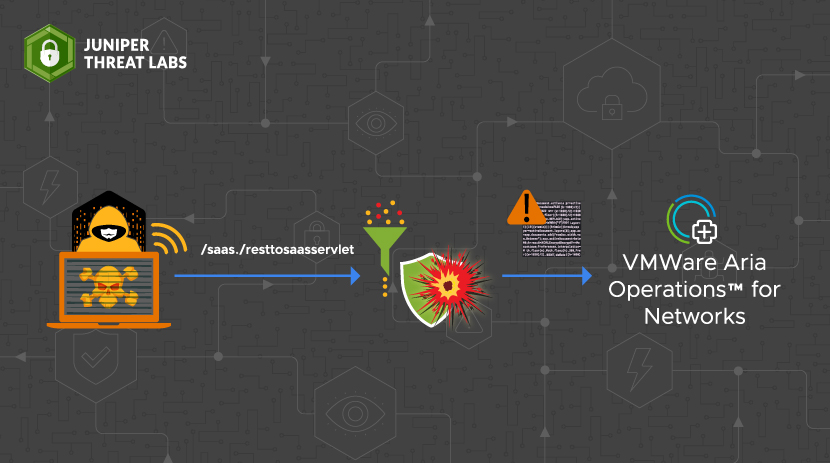
- CVE-2023-20887: VMware Aria Operations for Networks Unauthenticated Remote Code Executionby Ashish Joshi on September 20, 2023 at 7:56 am
HPE Juniper Networking Blogs CVE-2023-20887: VMware Aria Operations for Networks Unauthenticated Remote Code Execution VMware Aria Operations for Networks is a network monitoring and management tool used to build and manage an optimized, secure network infrastructure. A command injection vulnerability has been recently reported The post CVE-2023-20887: VMware Aria Operations for Networks Unauthenticated Remote Code Execution appeared first on HPE Juniper Networking Blogs.
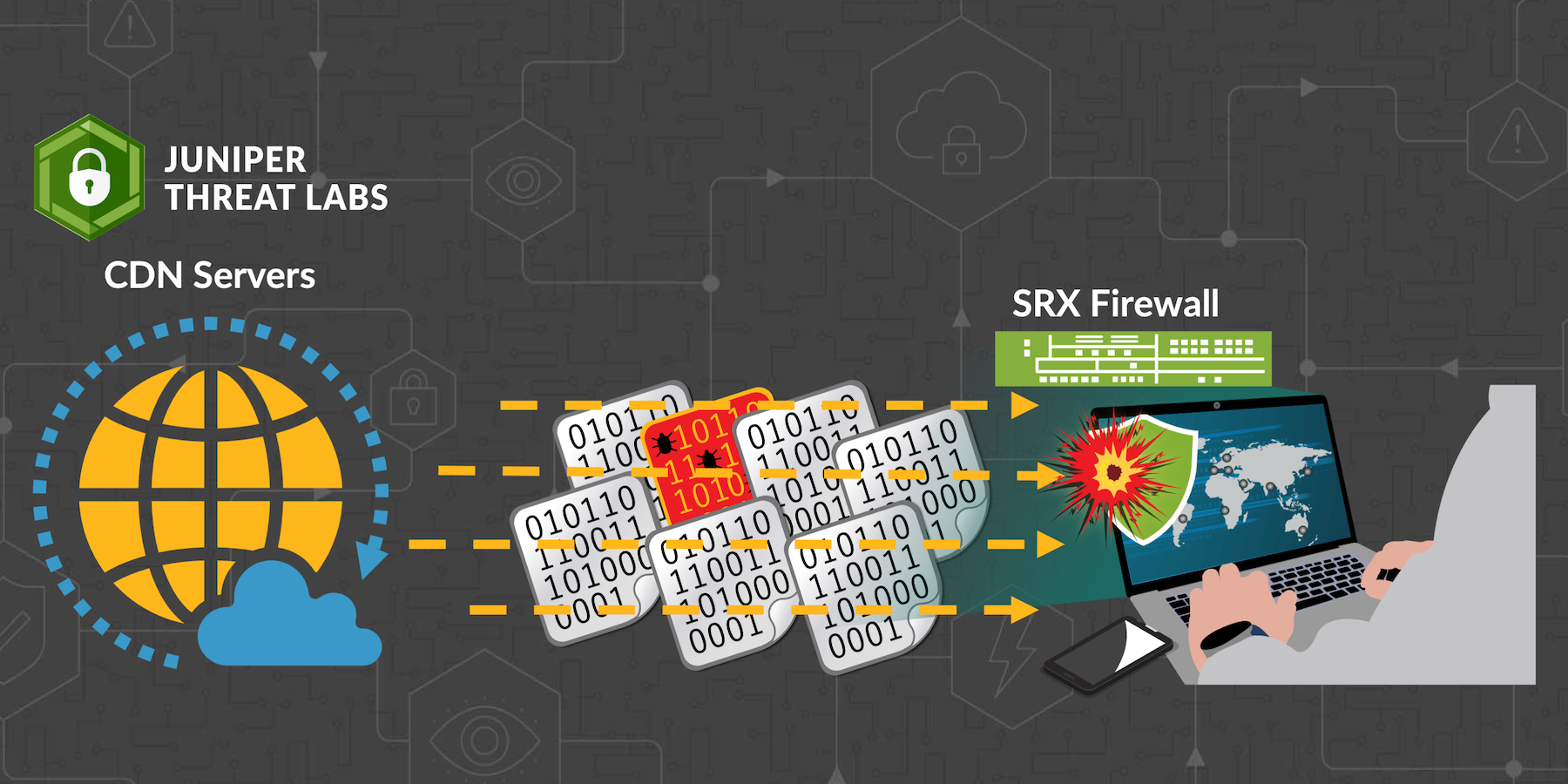
- Abused CDNs: From Speedy Content to Stealthy Malwareby Omar on September 5, 2023 at 6:19 pm
HPE Juniper Networking Blogs Abused CDNs: From Speedy Content to Stealthy Malware The global internet relies on Content Delivery Networks (CDNs) to deliver a seamless web experience for users. Because of the shared nature of a CDN’s resources, network operators must be The post Abused CDNs: From Speedy Content to Stealthy Malware appeared first on HPE Juniper Networking Blogs.
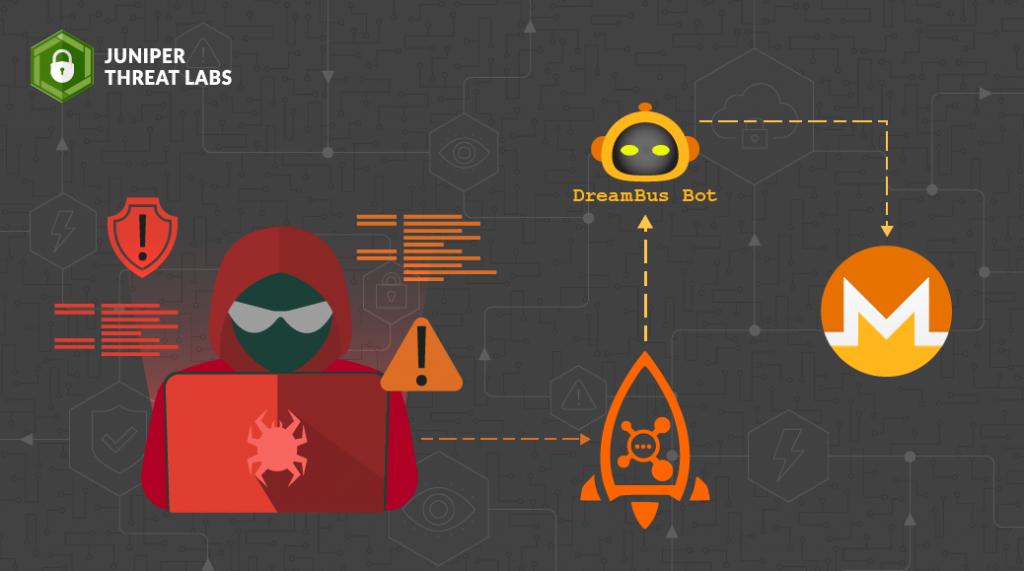
- DreamBus Botnet Resurfaces, Targets RocketMQ vulnerabilityby Paul Kimayong on August 28, 2023 at 1:00 pm
HPE Juniper Networking Blogs DreamBus Botnet Resurfaces, Targets RocketMQ vulnerability In May 2023, a vulnerability affecting RocketMQ servers (CVE-2023-33246), which allows remote code execution, was publicly disclosed. In a recent blog post, Juniper Threat Labs provided a detailed explanation of The post DreamBus Botnet Resurfaces, Targets RocketMQ vulnerability appeared first on HPE Juniper Networking Blogs.